Overview
Emu8086 combines an advanced source editor, assembler, disassembler, software emulator (Virtual PC) with debugger, and step by step tutorials. This program is extremely helpful for those who just begin to study assembly language. It compiles the source code and executes it on emulator step by step.
Inspect
Once you open the app you will see a registartion button
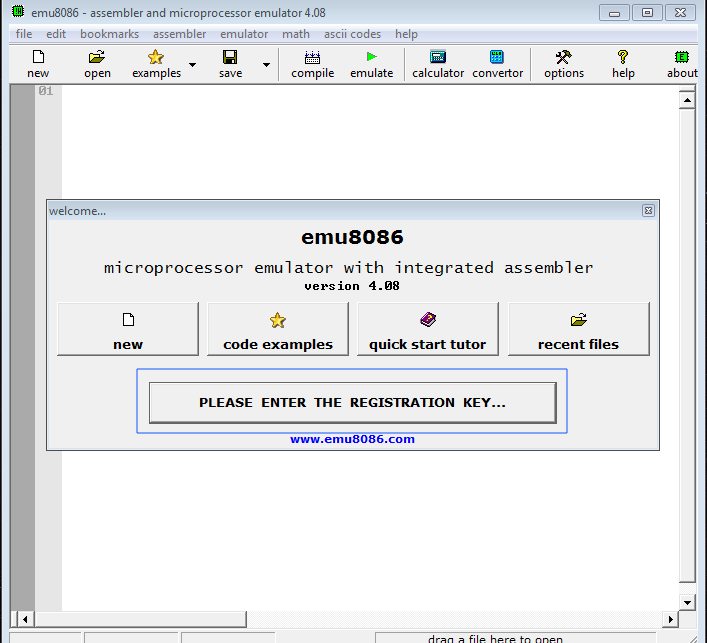 main window
main window
Click the button will open a small window with another button to buy a license with the followin links
1
2
3
https://shopper.mycommerce.com/checkout/product/2189-7
https://shopper.mycommerce.com/checkout/product/2189-9
https://shopper.mycommerce.com/checkout/product/2189-11
All of them are not working and i have done some search to make sure that this program is not maintained any more
 Links
Links
Fishing out inspection by trying to register with dummy name and key
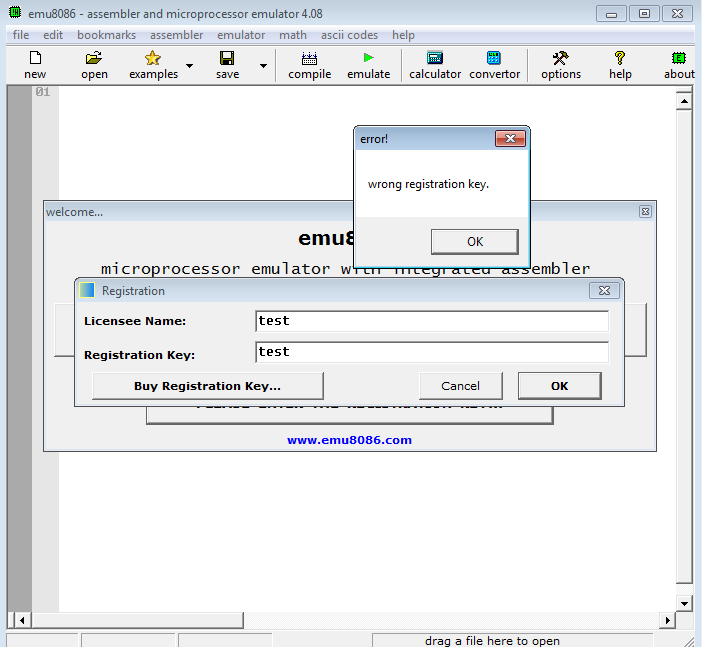 Register with dummy key
Register with dummy key
x32gdb
Start x32gdb while emu is running and attach it to the the debugger
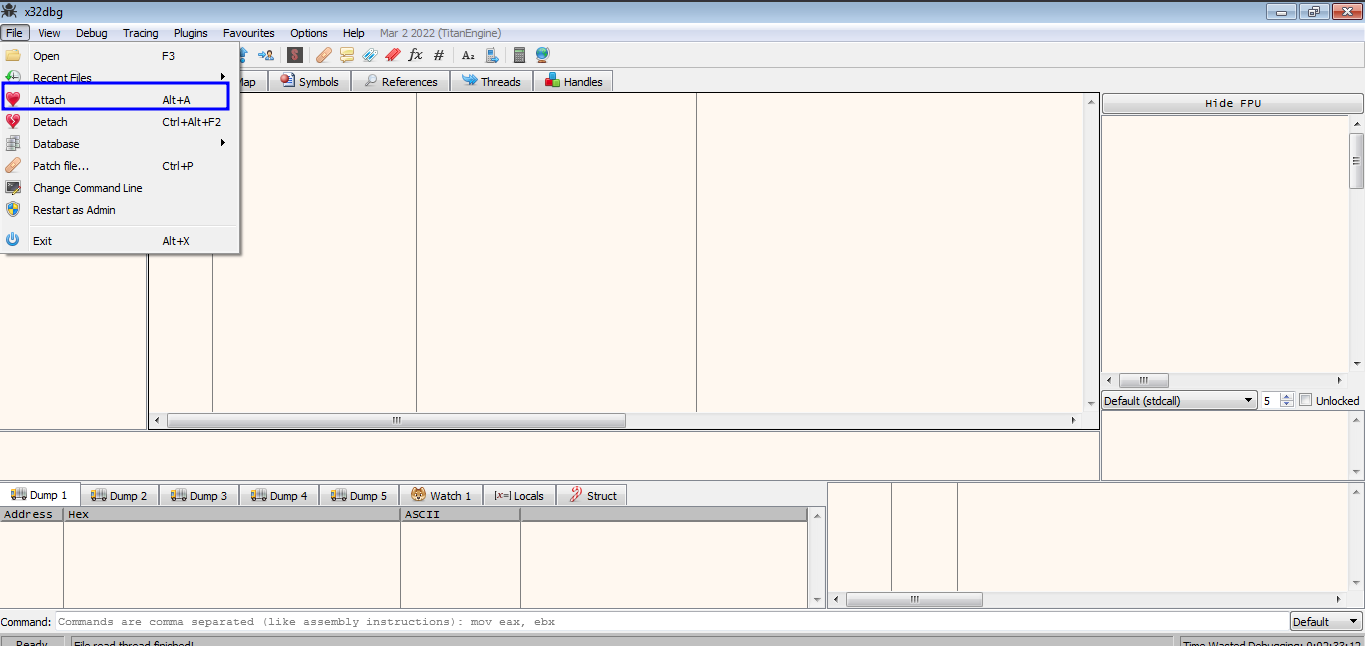 Attach to debugger
Attach to debugger
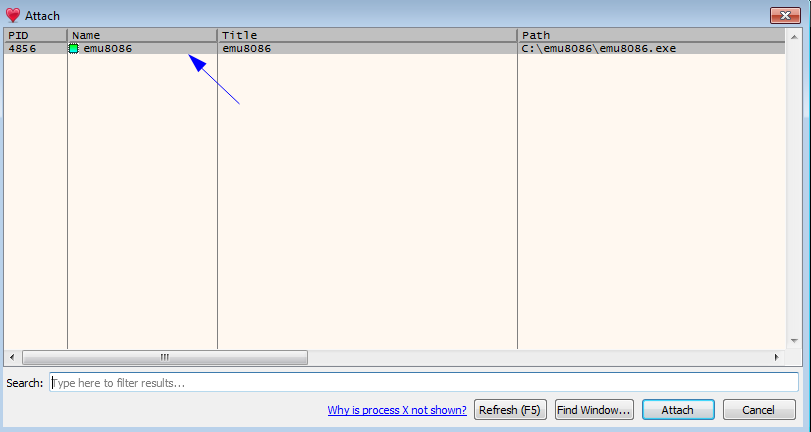 Select program to attach
Select program to attach
Then from select view -> Modules to list all the loaded modules
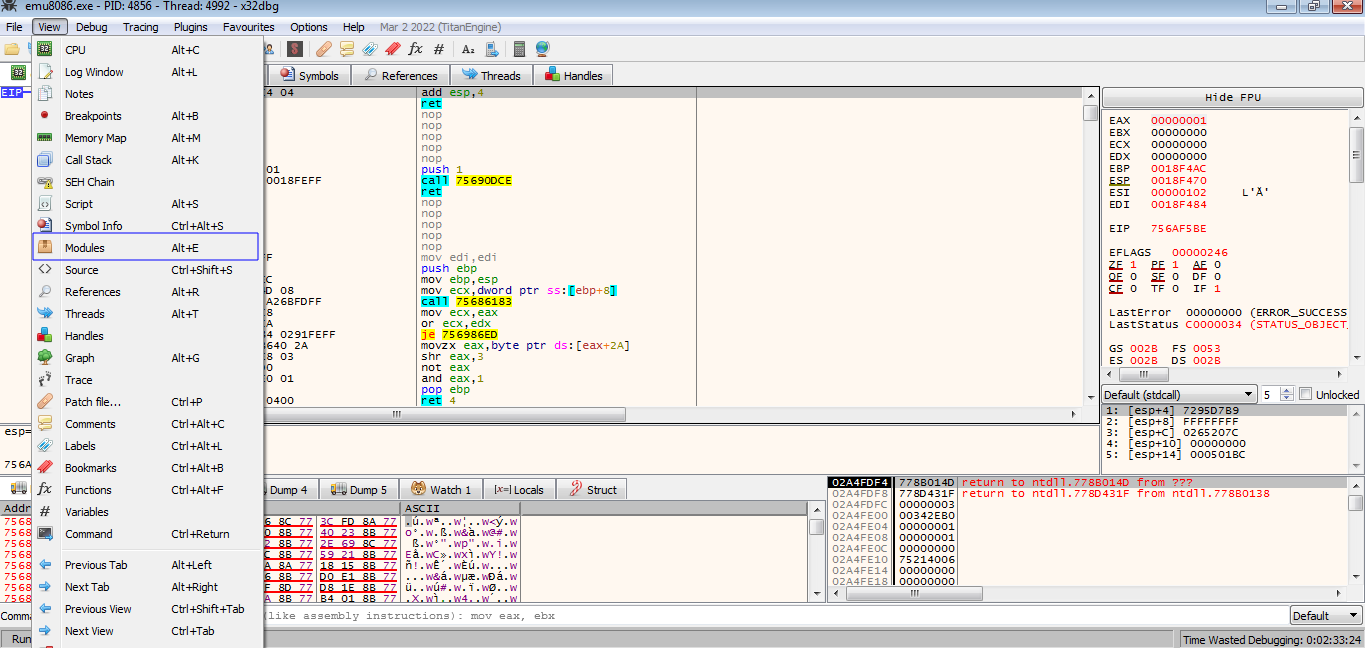 Modules
Modules
After this double click emu8086.exe
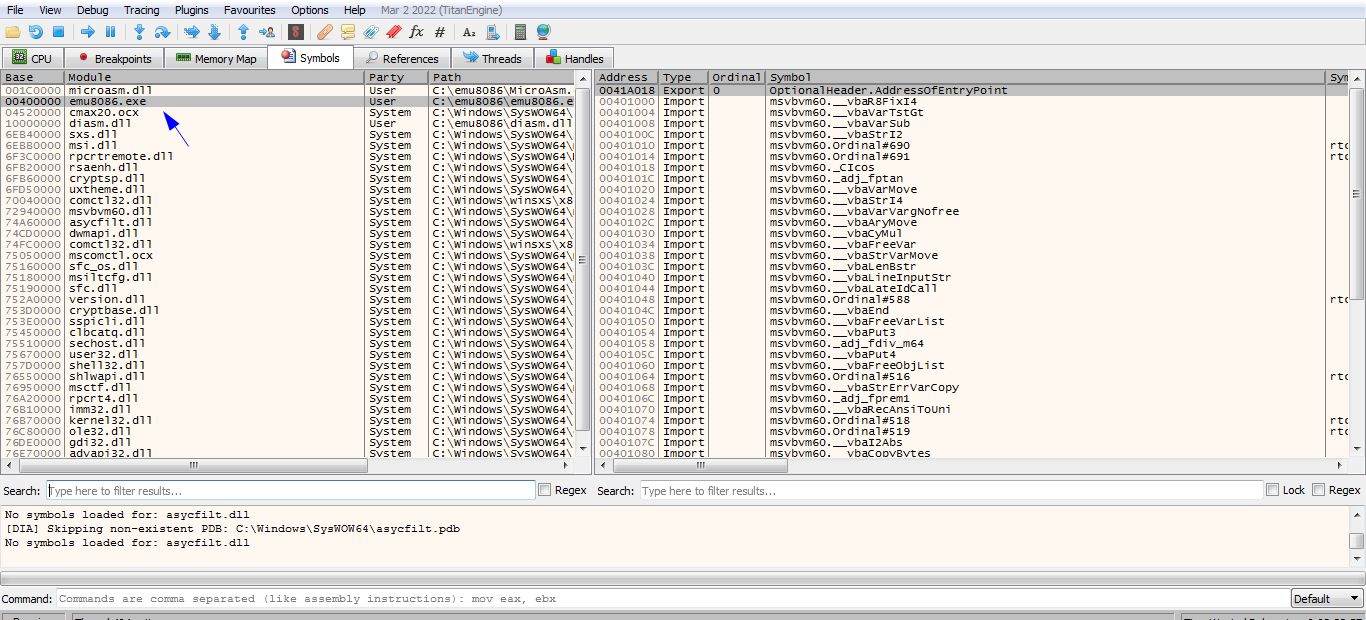 emu8086.exe
emu8086.exe
Now right click search for -> current module -> string refrences
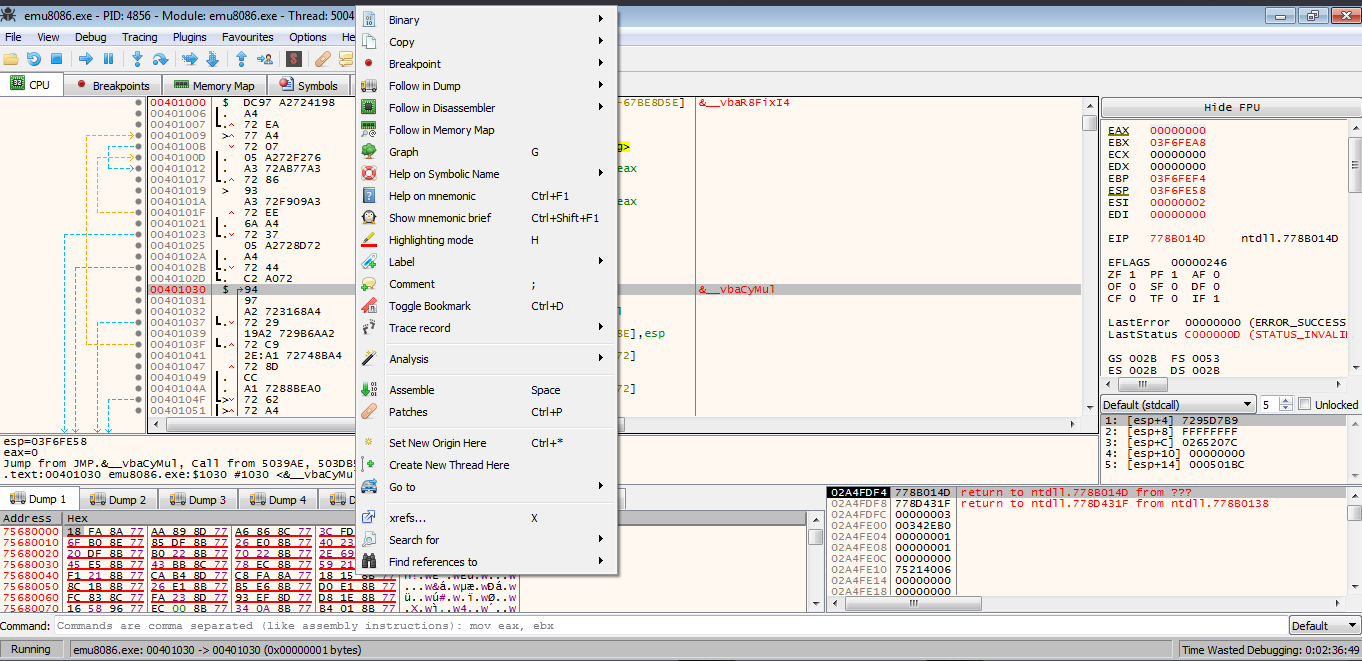 find strings
find strings
Seaching for Wrong registartion key as this message was shown to us
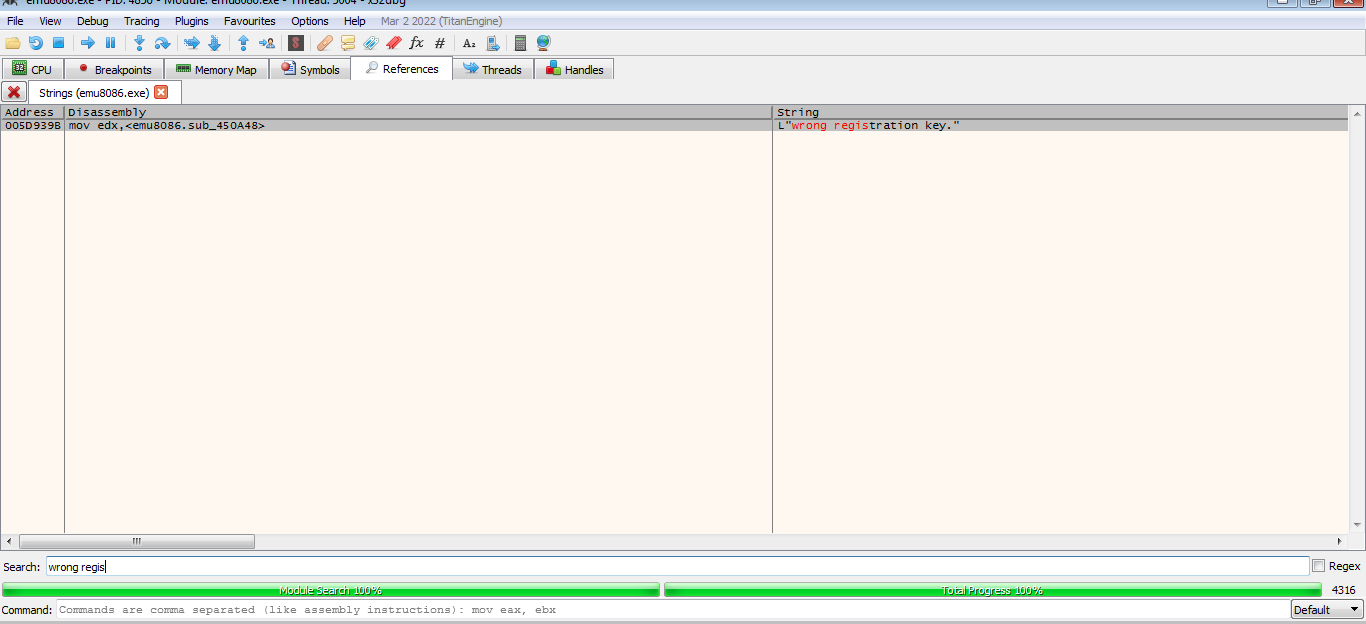 find registartion string
find registartion string
Double click it to show it in the program assembly and pressing Ctrl+A to analyze the module
And notice there is a jump to the instruction just before our string usage
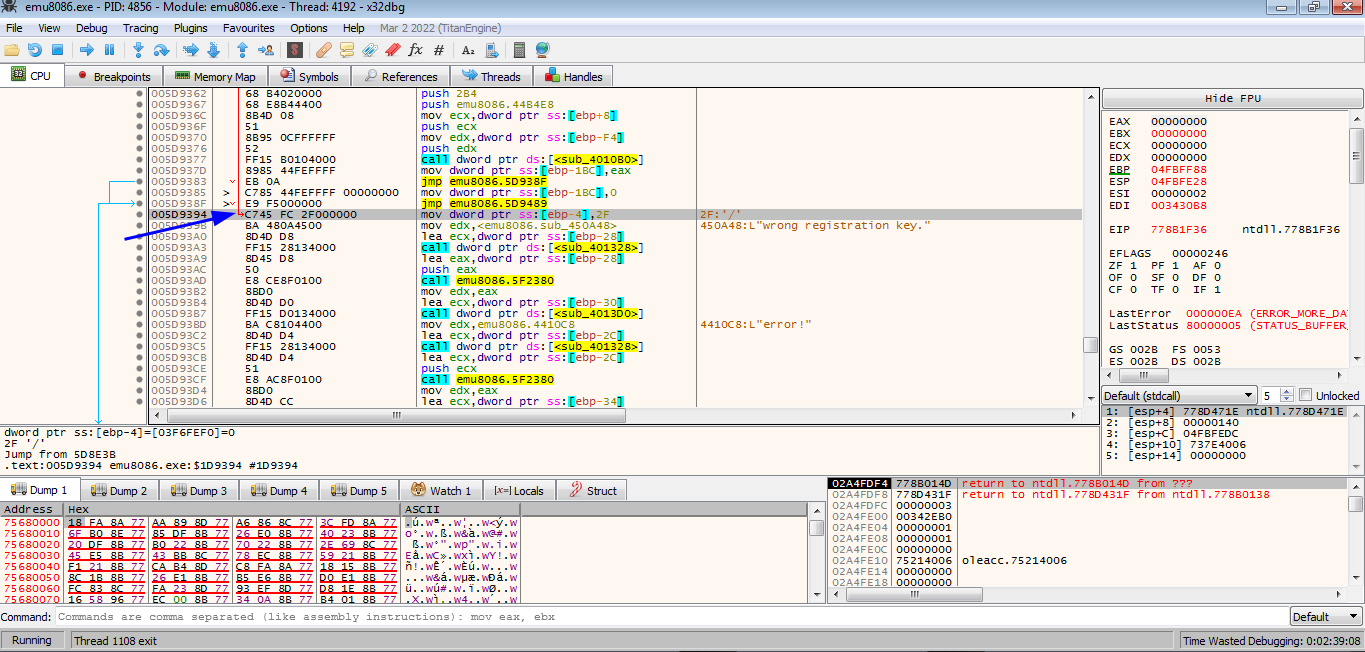 jump destination
jump destination
Scrolling to the jump instruction and the jump is based on a value stored at the address 621470
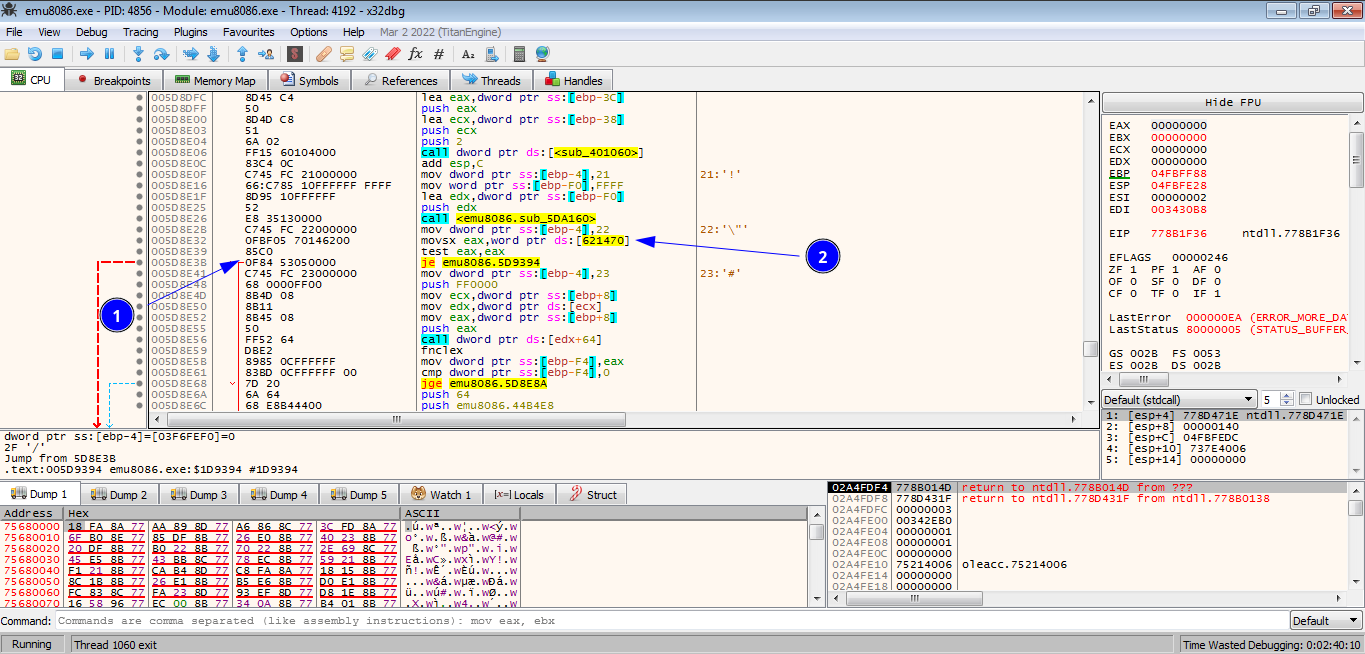 jump source
jump source
Right click the address select follow in dump -> constant emu8086.00621470
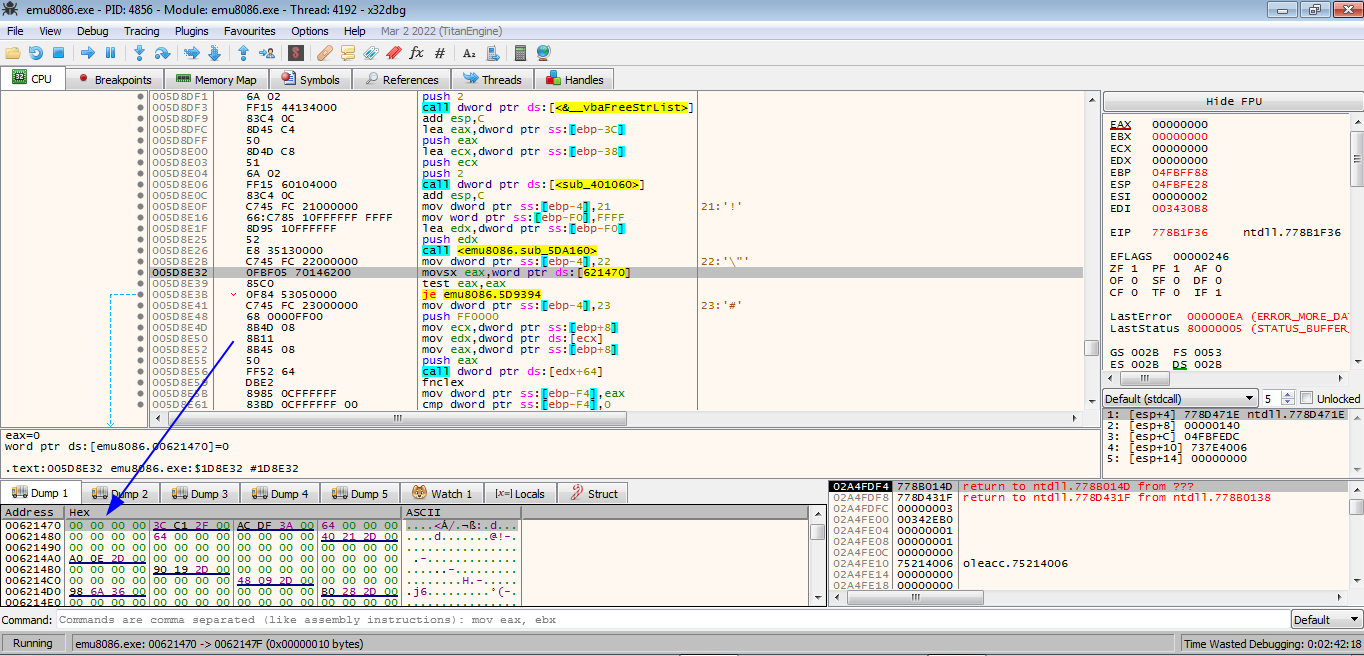 memory value
memory value
Right click the memory and search for refrences
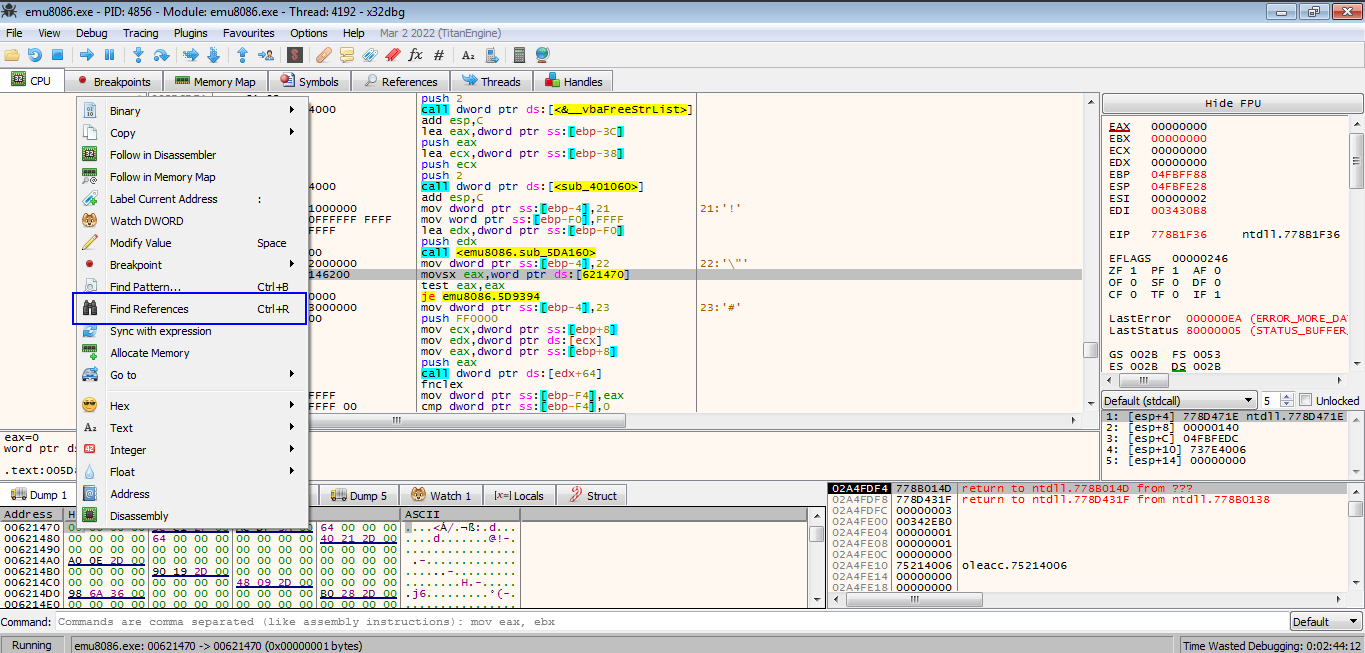 Find Refrences
Find Refrences
The last refrence is looking promising ;)
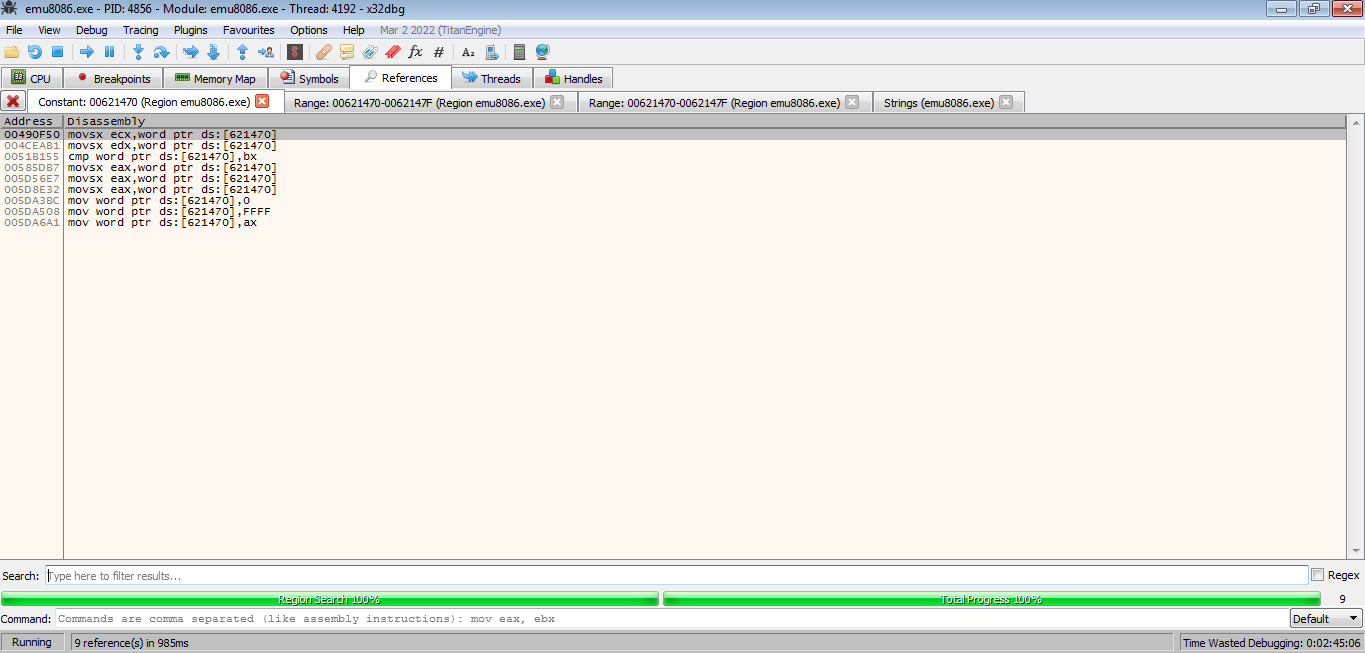 Refrences List
Refrences List
Follow it in assembly and here we find a function call just before it that took our username and key before
And followed by 5 bytes before writing ax to the memory
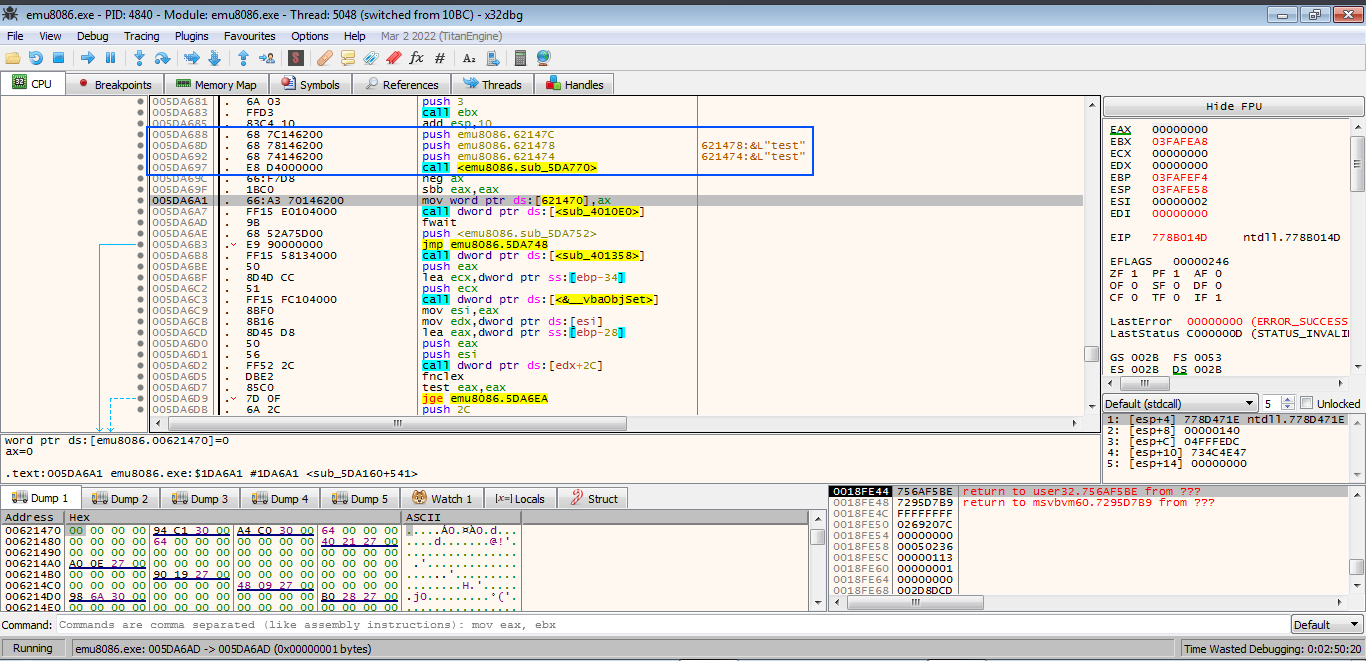 Verification function call
Verification function call
Using online assembly to opcode defuse with this instruction mov ax, 0xFFFF to set value 0xFFFF at ax register
The opcode of it is 66B8FFFF and this can be written into 4 bytes but we have 5 and leaving the last byte will misinterpret the next instruction so we batch it with 0x90 opcode of no operation nop
To edit press Ctrl+e
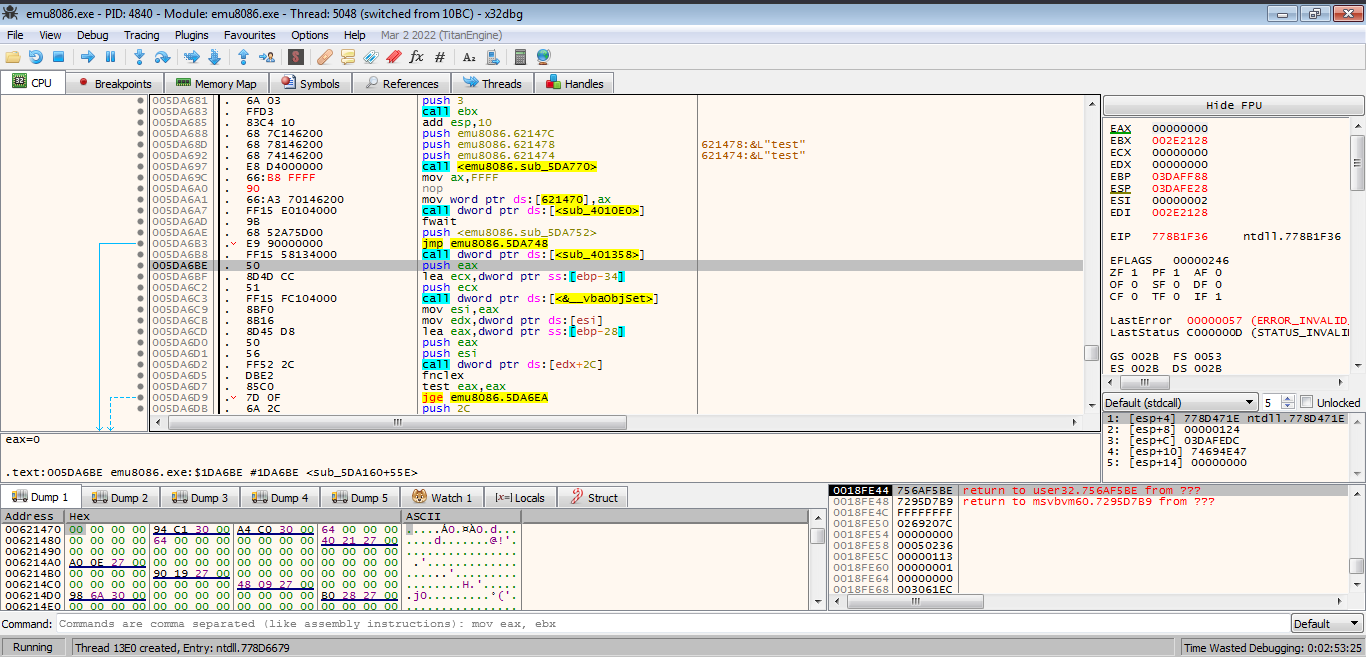 Patch emu
Patch emu
Apply the patch and start the patched version and suddenly it is register to test but how did it knows
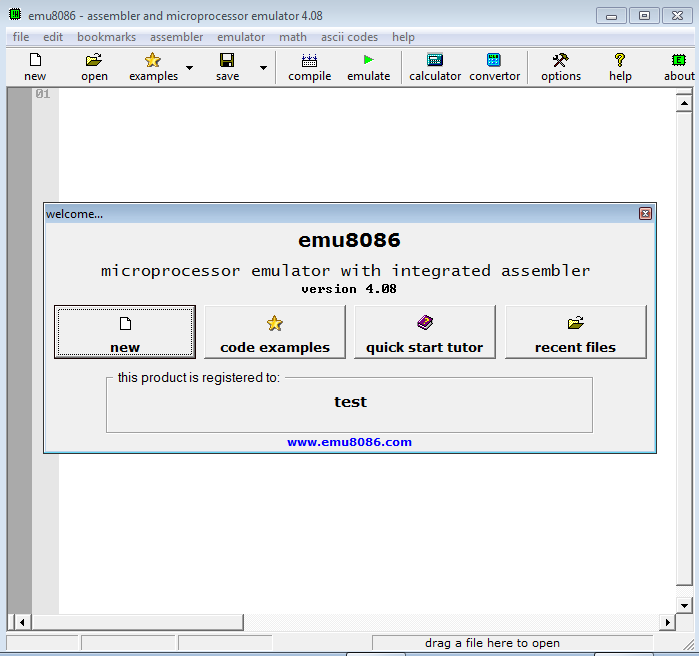 Registered to test
Registered to test
Looking at the emu files and file called reg.ini newly created and contain user name and key from our first attemp
Assume that it will read the file each time it start and check if username and key sotred in it are valid
Change the name at this file will change the name at the program ;)
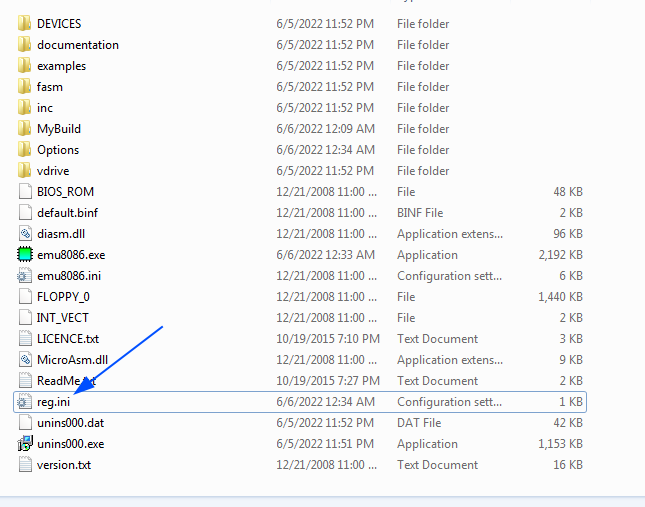 reg.ini
reg.ini
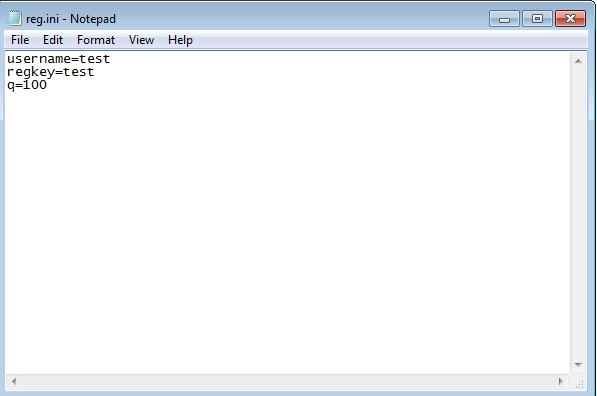 reg.ini
reg.ini
Create Patch With C
Open the patched version with hxd and search for 66 B8 FF FF to get the offset of the them on the exe
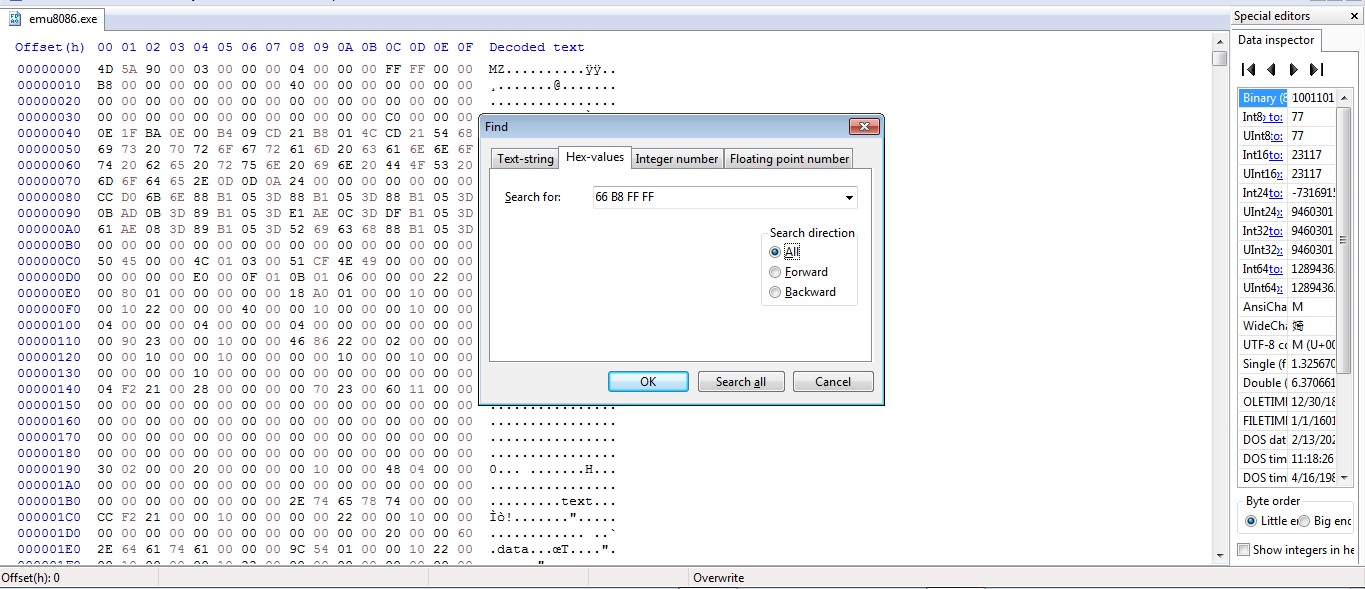 hxd
hxd
The offset is 0x1DA69D
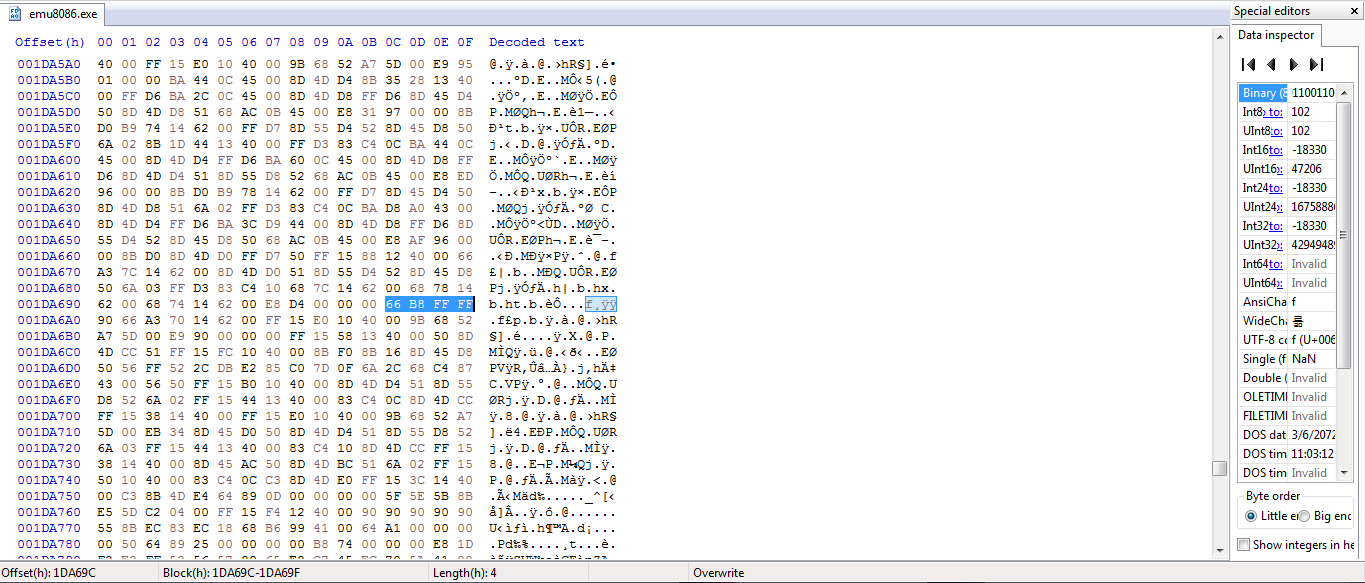 offset
offset
Write a c prgram to open the exe and move to our offset
1
2
3
4
5
unsigned char bytes[] = {0xB8, 0xFF, 0xFF, 0x90};
int offset = 0x1DA69D;
FILE *fileH = fopen ("emu8086.exe", "r+");
fseek(fileH, offset, SEEK_SET)
After this write our bytes
1
fwrite(&bytes, sizeof(bytes), sizeof(bytes[0]), fileH)
And for fun open reg.ini and write my name ;)
1
2
3
4
char reg[] = "username=Patched By Mahmoud Ramadan\nregkey=x\nq=100";
FILE *fileH2 = fopen ("reg.ini", "w");
fwrite(®, sizeof(reg), sizeof(reg[0]), fileH2)
Find full patch code at emupatch
Test the patch and it works
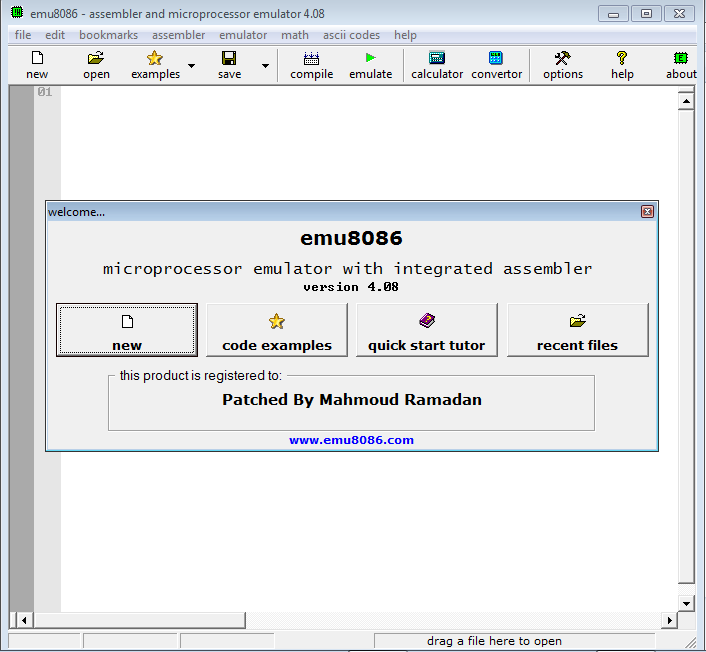 patch test
patch test