Initial Assessment
Sample Info:
MD5: b66eb4bcb2860ef48afbc1378e1ae545 File Type: PE32 Compiler Time Stamp: 2016-03-29 23:03:35
Sections
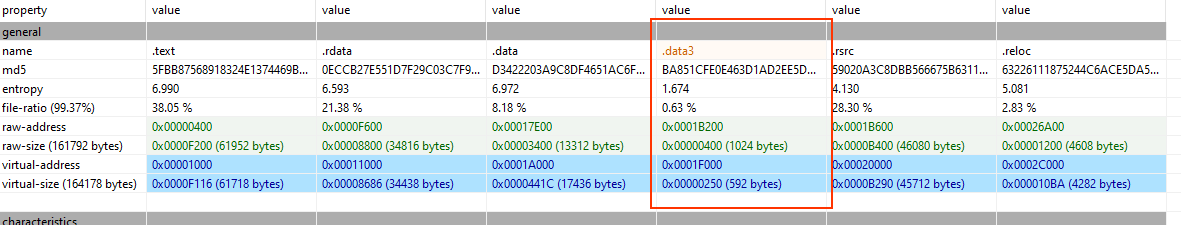
contains abnormal section name
Imports
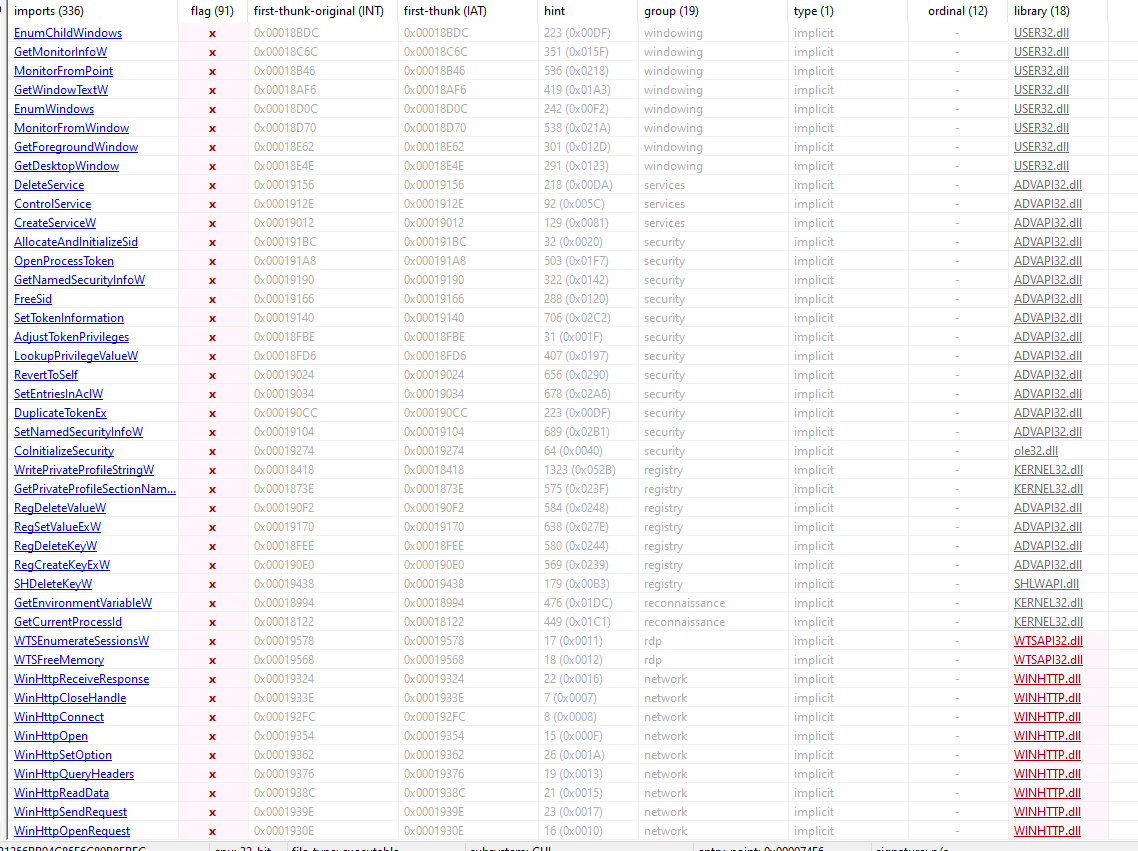
a lot of suspicious imports related to registries and internet connection but nothing related to cryptography
Strings and Resources
No important strings or resources was found in the sample
Entropy
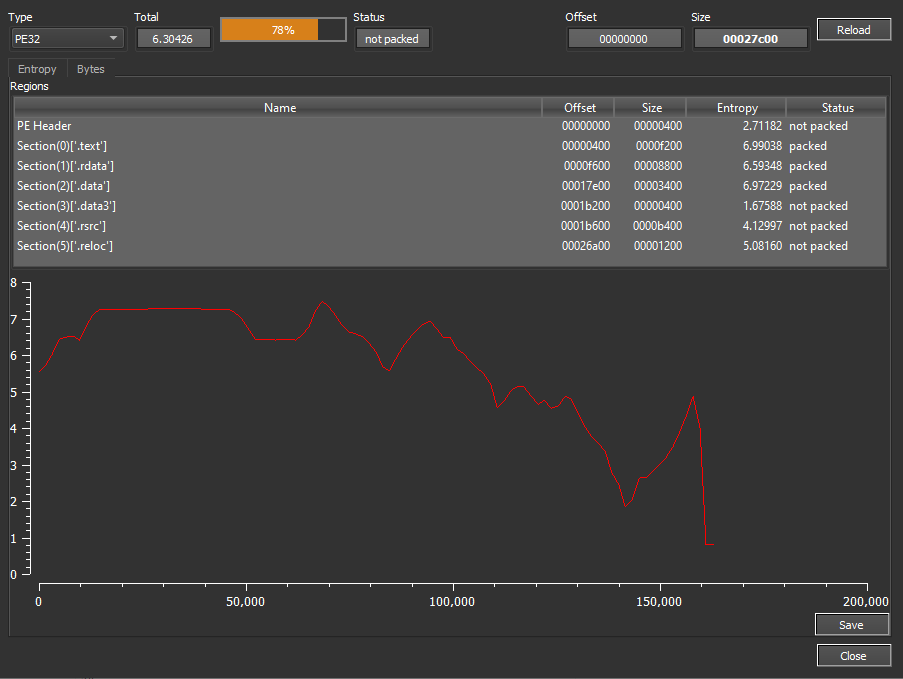
And now we sure that the sample is packed
Unpacking using x32gdb
Start by adding break point at virtualalloc and virtualprotect
1
2
bp VirtualAlloc
bp VirtualProtect
and hit run f9 to get to the entrypoint and once more to hit one of our breakpoints
It hit VirtualAlloc
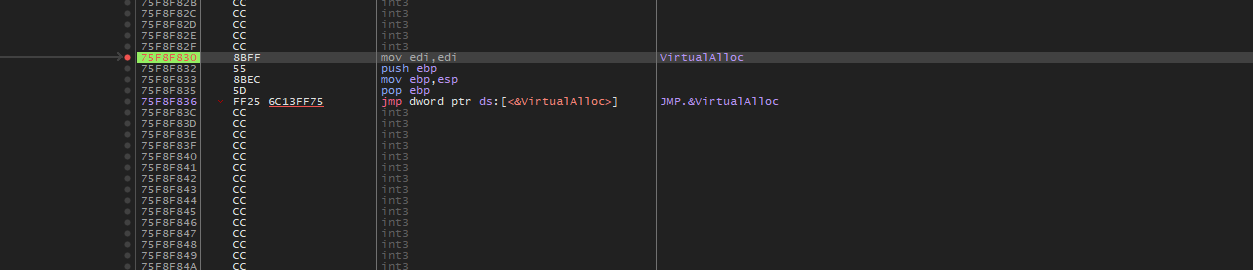
i will follow the jump to change the breakpoint of the VirtualAlloc from the beginning to the ret statement
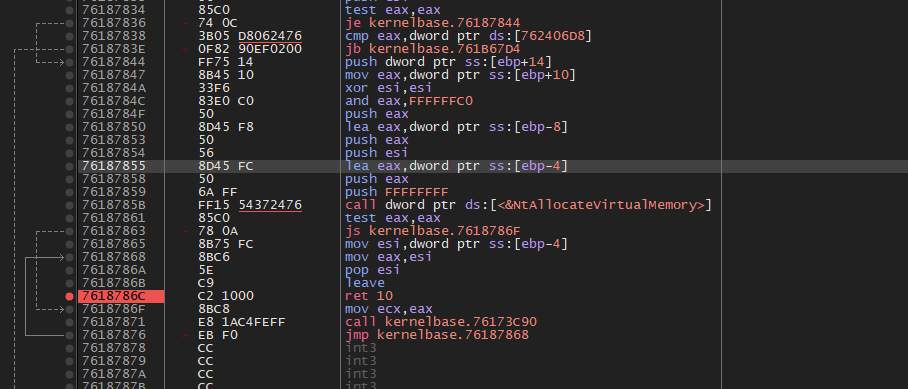
now when the breakpoint is hit Imgs

we can right click on the address and follow it in Memory Dump 1 Then hit run again now and the same break point in triggered again when when looking at Dump 1

Dump 1 looks like it contains a shellcode follow the new address at Dump 2 and hit run and the scenario repeat itself new memory is allocated and Dump 2 filled with some bytes that maybe a shellcode
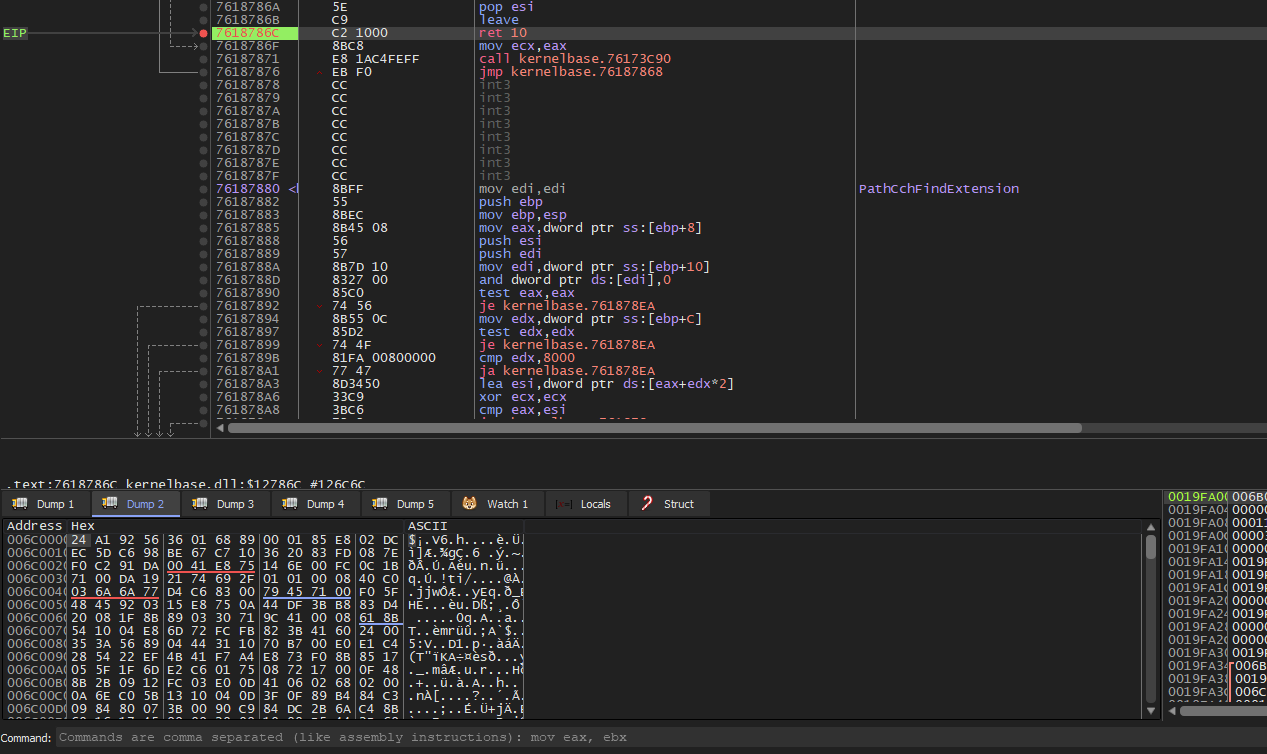
follow the new memory at Dump 3 and run and again new memory and the old is filled with same data as Dump 2
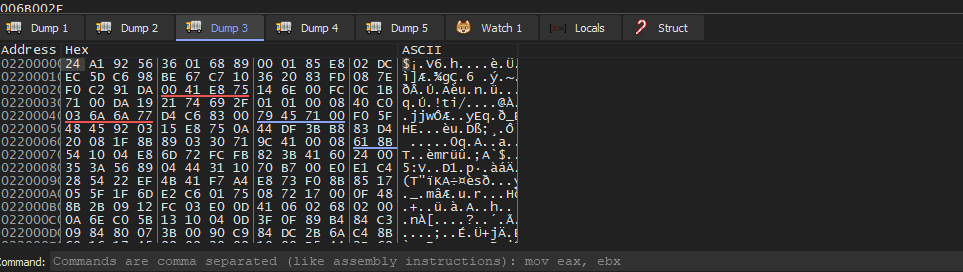
follow new memory at Dump 4 and run
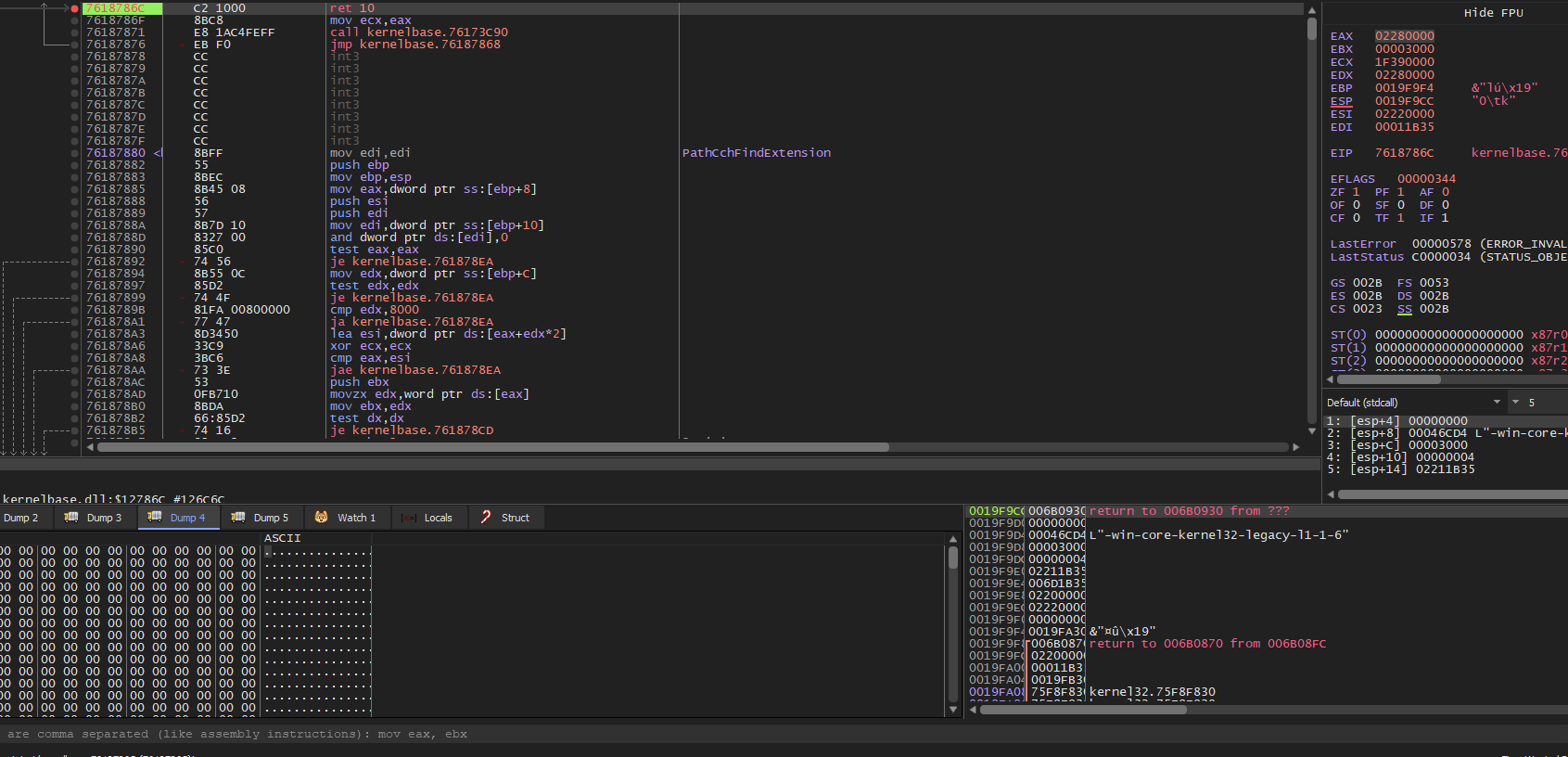
and now a new memory to allocate but the old memory is not written yet hit a run again it allocate a new memory the same address as the one we follow in Dump 4 so maybe this region was freed in the middle of the execution
follow the new address at Dump 1 and run
now we hit virtual protect
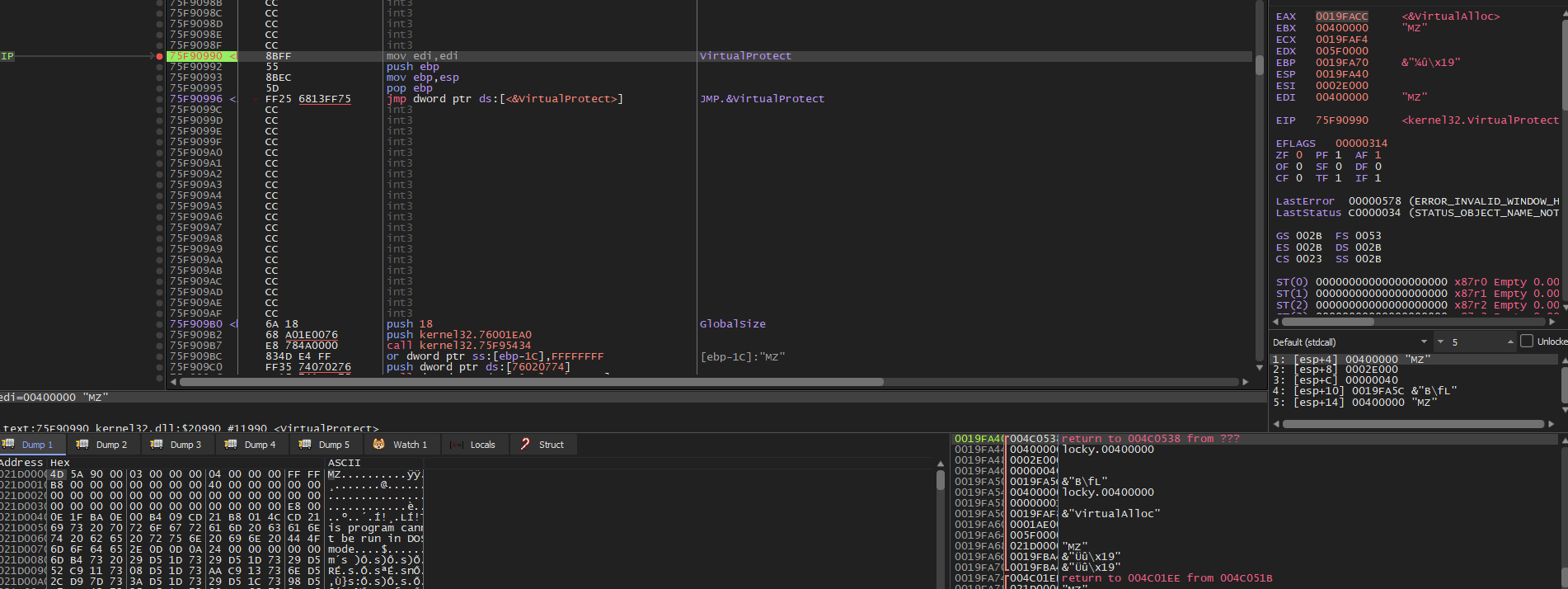
and the memory at Dump 1 is filled with PE File
now we can right click on the address and follow in memory map
and from memory map right click and dump to file
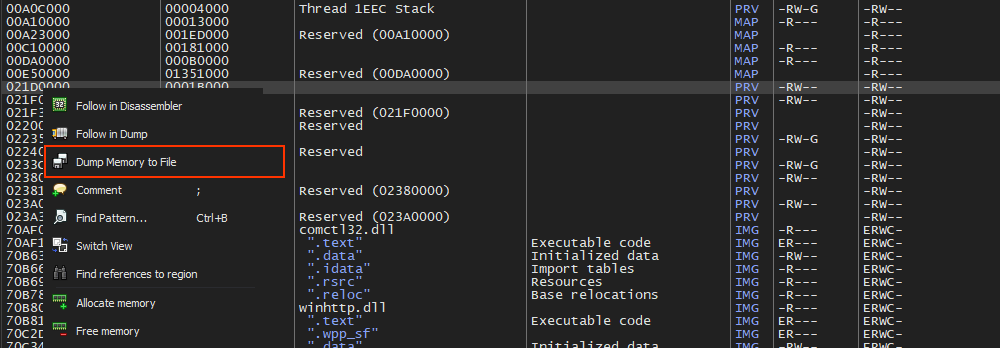
Now if we look at the unpacked file it is a valid PE32 file and contains more suspicious strings and imports